Traditionally, enterprise technology security was fairly simple to provide, because all systems were physically located in one place. IT security settings, such as a firewall, or identity and access management, were trivial to implement. And as everything was in one physical place, potential computer attacks could only happen in one place. The concept of traditional cybersecurity is therefore mainly based on trust and verification. But these days, that’s far from enough!
In 2021, it is no longer true that all IT equipment is found within a corporation. A lot of work is now done outside the physical framework of a company; emails, remote work via a laptop or cell phone, the use of residential Internet networks, and so on, all now need to be taken into account. This evolution in technology and work habits has contributed to the advent of the cybersecurity concept of “Zero Trust.” This philosophy relies on never trusting and always verifying, and was discussed during our webinar on May 6th 2021.

What Is The Zero Trust Concept?
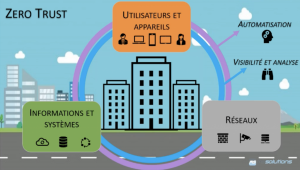
Zero Trust is a strategic approach to cybersecurity that emphasizes that trust is no longer something you can rely on outright. This security practice can be applied to 3 main sectors.
The Zero Trust model means questioning all presumptions of trust, in the face of all attempts to connect or access the services and technologies of an organization. In this way, it becomes possible to strengthen cybersecurity and ensure control over the accessibility of a network and its content, according to, for example, the position held by the person and their security profile.


Why Implement Zero Trust?
Cybersecurity according to the Zero Trust model brings several benefits:


One of the most important benefits is the ability to see all activities that take place in an IT infrastructure, whether performed inside the company or outside. The Zero Trust model allows for the monitoring of all actions in real time, but also allows you to trace past actions in the event of a computer incident. Activities are therefore monitored, so that the system is able to detect anomalies or incidents. A good example of an anomaly detected by the Zero Trust model would be a so-called abnormal connection attempt. For example, an employee may be connecting to the corporate network from Canada, but suddenly the computer system receives a connection attempt for that same employee, but from Finland. The system will then be able to alert the specialists, to determine if this connection is legitimate or an incident to be quickly avoided!
The Zero Trust concept can be of great benefit to your cybersecurity. However, its implementation can be complex and technical. This is why it is essential to call on a specialist in the field and be aided throughout the implementation of the Zero Trust concept in your business, for it to be a real success.
In short…
Implementation of the Zero Trust concept for your cybersecurity should be seriously considered. This will not only provide you with cybersecurity for your offices, but also for all your employees currently working from home. If you have any questions about how the Zero Trust concept can be implemented in your home or business, consult one of our specialists at MS Solutions now!