IT News
Microsoft 365: Reduce your mental load at work
This article does not claim to revolutionize mental health at work. Mental workload is a complex subject that requires comprehensive and personalized support. However, everyday tools, like those presented in…
Optimize your productivity with Copilot training for M365
Copilot for Microsoft 365 is a revolutionary tool, powered by cutting-edge artificial intelligence (AI), that integrates directly into your Microsoft ecosystem. Imagine having an intelligent assistant at your side, accessible…
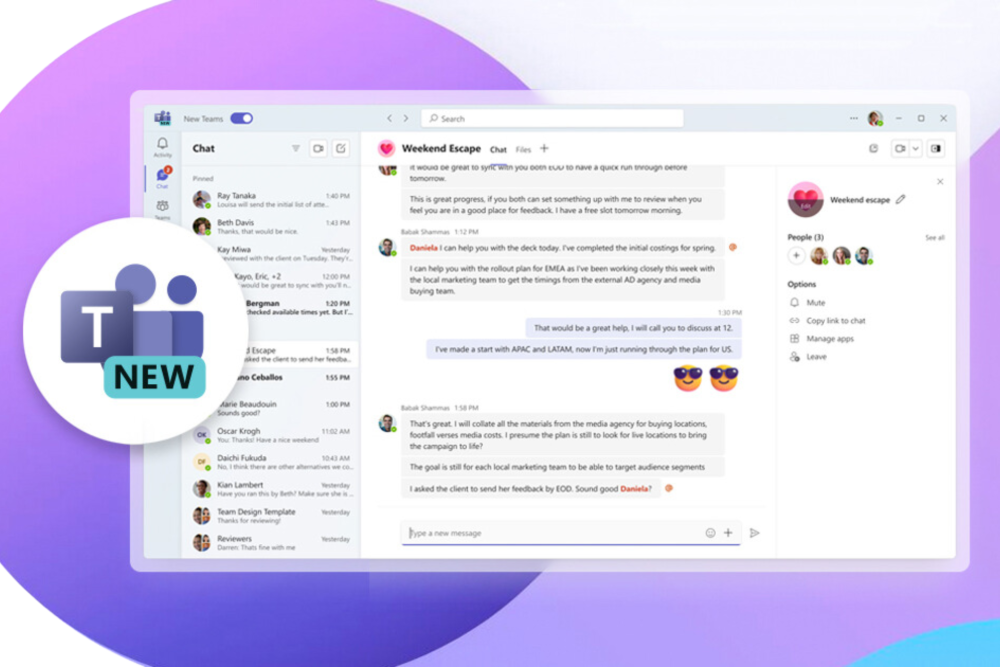
New Microsoft Teams: A redesigned collaboration experience
Microsoft Teams has a new interface and new features, providing a smoother and more efficient collaboration experience. This major update, called New Teams, gradually replaces the classic version of the…
MS Solutions talks about cybersecurity & new cyber risk trends in Business
The Journal Les Affaires published on October 12, 2023 a report on cybersecurity featuring Bernard Després, Partner, Security and Audit Practice Director at MS Solutions, who talks to us about…
Protect your communications: email encryption and best practices
In the digital age, email security has become a major concern. With cyber threats and hacks on the rise, it is essential to take steps to protect your online communications.…
Copilot in Forms: Create effective forms in the blink of an eye
Have you ever dreaded creating forms? Finding relevant questions, formulating options and formatting them can be tedious and time-consuming. Luckily, Copilot in Forms is here to make your life easier!…
MDR: Your shield against cyberthreats
Faced with the explosion of cyber threats in Canada, should businesses be worried? In 2023, Canadian businesses suffered an average of 72 attacks per week, according to Statistics Canada. This…
Protect your sensitive communications with Purview: Why email encryption is crucial.
Immerse yourself in the daily hustle and bustle of business, where every email click can potentially expose critical information to unwanted risk. Picture this: You’re the CFO of a growing…
Our news
MS Solutions talks about cybersecurity & new cyber risk trends in Business
The Journal Les Affaires published on October 12, 2023 a report on cybersecurity featuring Bernard Després, Partner, Security and Audit Practice Director at MS Solutions, who talks to us about…
MS Solutions finalist at Mercuriades 2024, “Innovation technologique” category
We are very pleased to announce that MS Solutions is nominated as a finalist in the prestigious Quebec competition of ✨Mercuriades 2024, in the “Technological Innovation”✨ category. This nomination represents…
MS Solutions announces the acquisition of Comtech
Quebec, January 25, 2024 – It is with pride that MS Solutions, a leader in digital transformation in Quebec, announces the acquisition of Comtech, an SME offering specialized services in…
MS Solutions among the 300 largest SMEs in Quebec in 2023
We have great news to share with you, news that has particularly special meaning for us at MS Solutions. Your unwavering support and our constant commitment have allowed us to…
Cybersecurity
MDR: Your shield against cyberthreats
Faced with the explosion of cyber threats in Canada, should businesses be worried? In 2023, Canadian businesses suffered an average of 72 attacks per week, according to Statistics Canada. This…
Prevention rather than cure: Backup and recovery strategies for your business
Backing up corporate data is an essential practice for ensuring business continuity, protecting sensitive information and minimizing the risk of data loss. Over time, backup methods have undergone significant evolution,…
Demystifying ISO 27001: MS Solutions’ Journey to Success
ISO 27001 remains the international standard for information security management. Compliance with this standard can strengthen a company’s resilience and increase the confidence of its customers, suppliers and insurers. Through…
Microsoft Intune: secure, centralized device management
In a world of constant technological change, where working patterns are shifting towards hybrid configurations, including teleworking, and where equipment is evolving rapidly, thanks in particular to the “bring your…
Vigilance: are you getting the most out of the platform?
Considering that 82% of security breaches in an organization are the result of human error (Verizon, 2023), and that 1 in 5 email attacks is successful (Tessian, 2022), it’s safe…
5 steps to block spam on Outlook
Unwanted e-mails, also known as spam, can be a major nuisance in your inbox. On an organization-wide scale, they can not only reduce your productivity, but also have an impact…
Penetration Testing or Cybersecurity Audit: Which is Right for Whom?
IT security is a major concern for all organizations, big or small. Cyberattacks are becoming more frequent and sophisticated, and the consequences can be disastrous. In this context, it is…
What are good data backup practices?
Data backup is crucial for any organization, regardless of size or industry. Data is often the basis of all business activity, and the loss of this data can have catastrophic…
Microsoft 365
Microsoft 365: Reduce your mental load at work
This article does not claim to revolutionize mental health at work. Mental workload is a complex subject that requires comprehensive and personalized support. However, everyday tools, like those presented in…
Optimize your productivity with Copilot training for M365
Copilot for Microsoft 365 is a revolutionary tool, powered by cutting-edge artificial intelligence (AI), that integrates directly into your Microsoft ecosystem. Imagine having an intelligent assistant at your side, accessible…
New Microsoft Teams: A redesigned collaboration experience
Microsoft Teams has a new interface and new features, providing a smoother and more efficient collaboration experience. This major update, called New Teams, gradually replaces the classic version of the…
Protect your communications: email encryption and best practices
In the digital age, email security has become a major concern. With cyber threats and hacks on the rise, it is essential to take steps to protect your online communications.…
Copilot in Forms: Create effective forms in the blink of an eye
Have you ever dreaded creating forms? Finding relevant questions, formulating options and formatting them can be tedious and time-consuming. Luckily, Copilot in Forms is here to make your life easier!…
Modern Work: How Microsoft 365 is revolutionizing collaboration
Organizations are navigating an ever-changing business landscape, where agile collaboration, flexible working and optimized productivity are imperative. In this era of accelerated digital transformation, technology tools play a crucial role…
SharePoint Intranet: boost your company’s collaboration and internal communication
Imagine a world where information is centralized, accessible in one click and where collaboration is seamless. This is the promise of the SharePoint intranet: a powerful solution to revolutionize communication…
Teams: 7 Steps to a Successful Webinar
It may be that you have been planning to provide training in your company, but have found yourself constrained because of recent circumstances. Meetings in person are currently prohibited, but virtual gatherings are not, and that’s great because we have…
Documents to download
Copilot for Microsoft 365: The optimal adoption journey
Fill the form to download the document
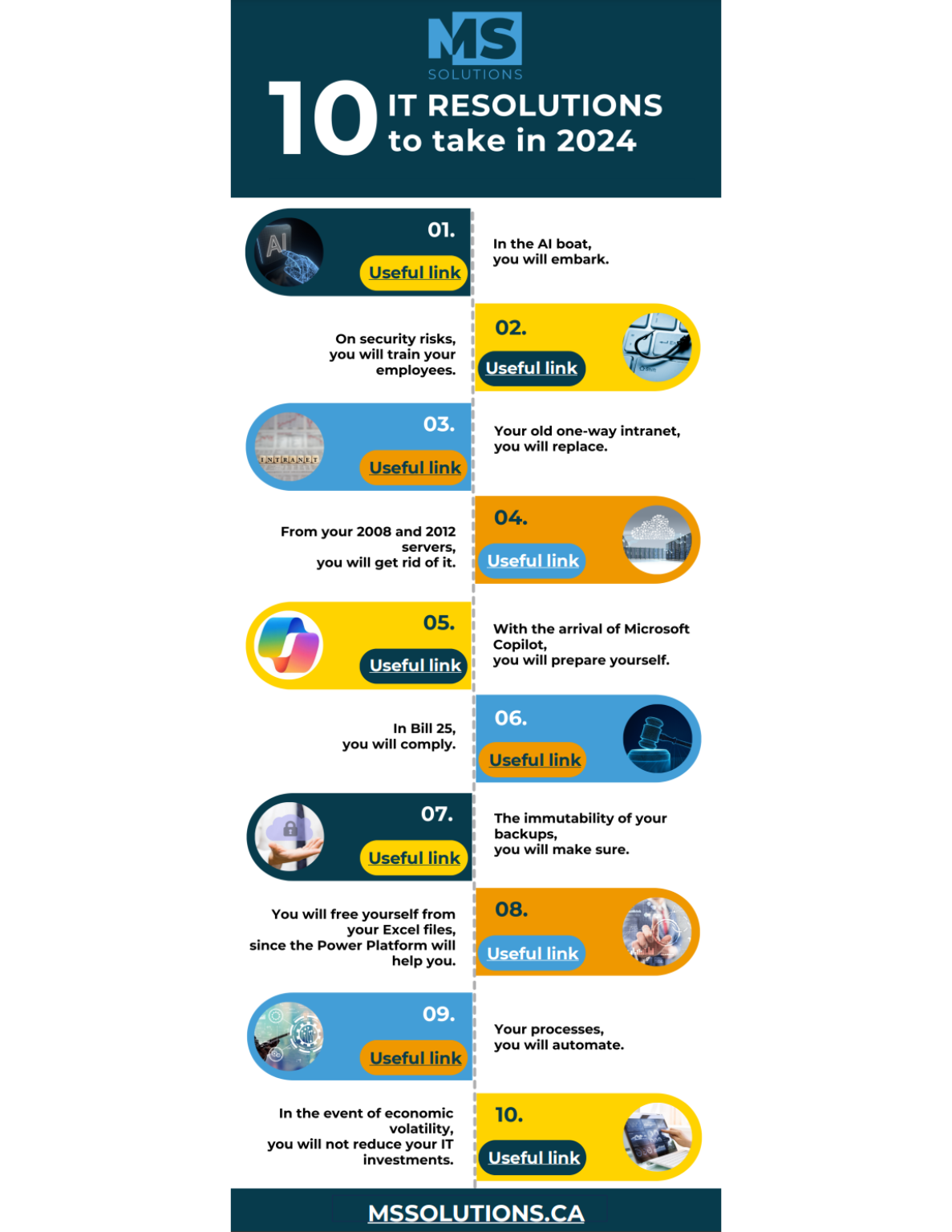
The 10 IT resolutions to make in 2024
Fill the form to download the document.
10 Essential Elements of Hybrid-Mode IT Strategy
Fill the form to download the document
The hot IT topics in the business world in 2023
Fill the form to download the document
Succeed in your Microsoft 365 journey
Fill the form to download the document
8 criteria for choosing a cloud provider
Fill the form to download the document
Emerging threats in cybersecurity: evolving to thwart threats
Emerging threats in cybersecurity: evolving to thwart threats Document to download Grab a coffee Get a quote Contact Services Secure IT Managed Services Training Cybersecurity for Companies M365 Consultation M365 Tools Secure cloud and infrastructure Audit and…