During our webinar on Friday, April 22, we discussed the importance of continuous phishing awareness. Thus, we took the opportunity to present our platform: Vigilance – whose goal is to keep employees in their journey to remain vigilant at all times.
Why promote continuous awareness
A few years ago, it was common practice to train employees once a year to be aware of the risks of phishing. Today, malicious individuals are using increasingly realistic schemes to phish their victims. As the threat is constantly evolving, maintaining a continuous awareness cadence keeps your teams alert to the risks to ensure that individuals are constantly vigilant.
A pragmatic approach in 5 steps
The Vigilance continuous awareness platform offers a pragmatic 5-step approach to survey your employees, train them, exercise them, and evaluate them, allowing them to progress continuously!
Step 1 – Initial survey
The platform offers your employees a 24-question survey to establish a risk profile.
Sample questions:
- Have you ever shared your work password with another person?
- In my role, is the information entrusted to be a target for criminals?
- Do you send or save work information to personal email accounts or store information on drives?
The platform determines from your employee’s responses whether they are already sensitive to cybersecurity risks and whether their behaviours are prudent or at risk.
Step 2 – Initial courses
Once the survey is completed, the user is invited to take the following 4 pieces of courses:
Cybersecurity 101: The World of Cybercrime
Cybersecurity 102: Hacking Humans
Cybersecurity 103: Malware
Cybersecurity 104: Protecting Yourself
Each course session teaches users about different aspects of cybersecurity. The manager can follow the employee’s evolution.
🌟 The little extra: In the “Marketplace” menu, you have access to a huge bank of cybersecurity courses that you can give your employees access to if you want. You might find some that are directly related to your industry sector.
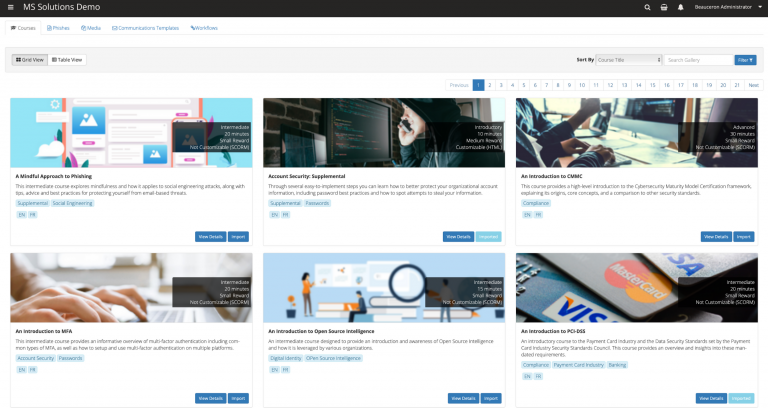
Step 3 – Basic simulation
Once the user has completed the 4 training sessions, a series of 3 simulated phishing emails is sent to him. The difficulty of the 3 emails varies to test the user’s knowledge and challenge him to learn how to spot and report a real phishing attack.
Warning: the simulations differ from one employee to another for greater efficiency!
Depending on the results obtained by the user, the platform continues to evolve according to the individual’s profile. Thus, he will receive emails of the same type as those where he was the least vigilant. On the other hand, it will propose new training courses related to his weaknesses to improve his skills!
The survey, the follow-up of the courses, and the employee’s reaction to the series of emails will allow establishing a risk score of the user.
Step 4 – Completion Survey
Team members receive a completion survey to assess their training and experience.
Sample questions:
- Do you understand the important role you play in protecting your organization from cybercriminals?
- Do you feel you know more about security as a result of this experience?
- Do you feel that your organization has provided you with enough information to protect yourself from cyber-attacks?
The responses from your teams provide managers and security awareness personnel in your organization with insight into the success of the initial training.
Step 5 – Continuous simulations
Once the completion survey is over, team members receive random, varied phishing simulations monthly or at the interval of your choice, which will be spread out over the rest of the year.
To reproduce a realistic environment and to sharpen everyone’s vigilance, the emails will simulate phishing scams of varying complexity and pattern. Your employees do not receive the same emails, and they do not receive them at the same time.
❤️ Favourite feature: During a phishing campaign, the employee can report an email that looks suspicious using a button linked to his Outlook email. When they report an email as being a risk, the platform receives the information and informs your employee’s vigilance rating if the reported email presents risks.
You can also choose to forward emails identified as at risk to the destination of your choice for analysis.
A progress tracking tool for the employee and the manager
The platform implements a risk score that ranges from 500 to 1000. A user around 500 is considered very safe and will represent a low risk to the organization. Conversely, the closer an employee’s score is to 1000, the higher the risk to the organization.
Your employees can consult their data via their dashboard, while you as manager, have access to the data of each employee.
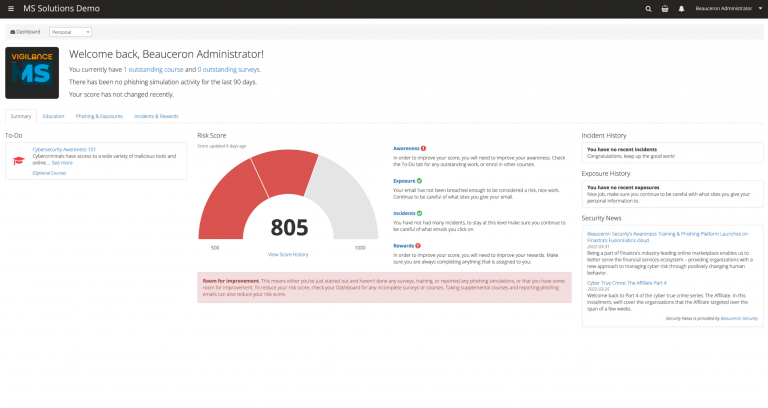
Employee dashboard:
Each employee can see his or her personal risk score and the items where he or she can improve.
Employees have access to courses and programs recommended by the platform so they can train and increase their skills.
Your employees can also view phishing emails they have received from the platform to see if their level of vigilance was correct for the situation.
Manager dashboard:
At the organizational level, as manager, you can see more metrics.
You can, for example, choose to divide your employees according to the segmentation that is most interesting for you: by departments, by geographical areas… This allows you to establish very precise statistics on the users of your choice.
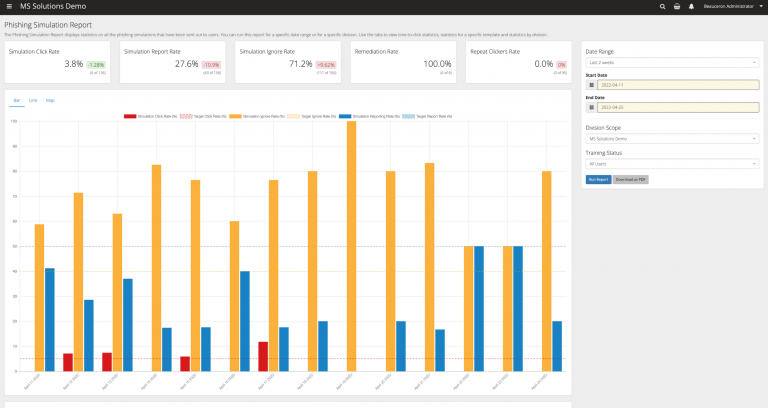
You can edit a wide range of reports in PDF format. This can be useful for example in a process of maintaining compliance with an ISO standard.
Reports example:
- Rate of people who clicked on a fraudulent link
- How many reported an email as “risky
- Rate of indifference to simulations
This way, you can see how well your outreach efforts are working.
As a manager, you can also access over 200 phishing email templates. The platform gives you the ability to edit them to make the email even more realistic!
To summarize the benefits of the Vigilance platform
- Continuous vigilance: Since phishing awareness is no longer a one-time event, it allows your team to maintain a continuous vigilance instinct, not just during the training period.
- Detailed analysis of results:
From your employees’ perspective, they can view their results and improve their cybersecurity skills.
From the managers’ point of view, you can have a global view of the organization or focus according to the chosen criteria. You can edit tracking reports to measure the impact of awareness efforts. - Identified and trained at-risk users: Managers can identify at-risk individuals and train them to reduce risk within the organization.
- A “Vigilance” Button in Outlook: This button is integrated into Outlook and acts as an alarm bell. It allows employees to report suspicious emails. The button communicates with the Vigilance platform and allows the risk rating of individuals to be reinforced (or not). Designated emails can also be forwarded to a destination of your choice for analysis.
- A fully bilingual (soon trilingual) tool: The platform is available in French and English. Phishing emails are also in the user’s language. Soon, it will also be available in Spanish.
- All-inclusive turnkey solution: Vigilance is a turnkey, all-inclusive solution. By subscribing to this solution, your team will have access to all facets of the phishing awareness platform:
- The educational part (courses bank)
- The immersive part (fictitious, but realistic phishing emails)
- Evaluation (initial survey, completion survey and ongoing evaluation)
- Follow-up (evaluation reports, risk rating)
In short
Hackers are evolving, and your awareness solutions must also become more sophisticated. The Vigilance platform is an investment for any business that wants to manage its risk properly. Engage the MS Solutions team to help you evaluate the best cybersecurity solutions for your business.




