Cybersecurity maturity diagnosis
Thanks to our cybersecurity maturity diagnosis, you will know where your organization is at in its journey towards optimal cybersecurity. This will make it easier for you to know what the next steps are to secure your organization.
Gain insight into your cybersecurity with our cybersecurity maturity diagnostic

Estimate

Strengthen

Propel
Where are you on your cybersecurity journey?
This safety journey, we see it as evolving, just like your organization.
We believe that this maturity scale is climbed little by little, by putting in place a roadmap of your cybersecurity strategies to grow in tightness, as in maturity, over a period that suits you.
As in everything, we start with the foundations to draw a more sophisticated approach over time.
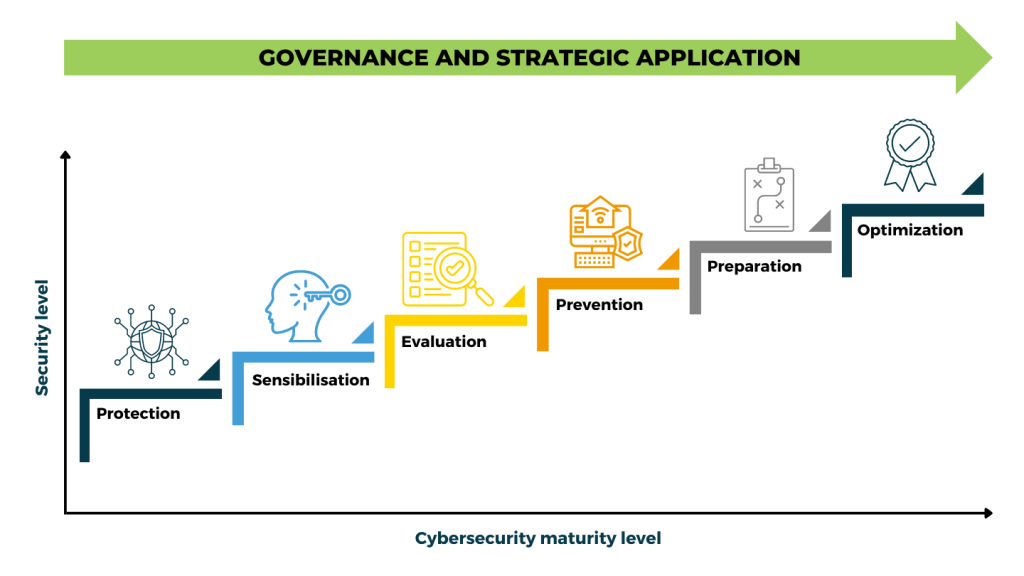
The protection phase makes it possible to lay the foundations of cybersecurity through various technological solutions.
- Multi-factor authentication
- Endpoint Detection and Response (EDR) Solutions
- Network Security Solutions (NDR)
- Advanced detection and response (MDR) solution
Cloud security also allows you to lay the foundation for protecting your technological environment.
- Secure cloud
- Microsoft 365
- Azure
The awareness phase helps integrate the human component into the cybersecurity journey, which is essential to educate users and keep them vigilant.
- Information Security Policies and Guidelines
- Staff training and awareness program
- Exercise and monitor user vigilance against threats
Although user awareness of external threats is very important, it is also important to be equipped and to promptly detect leaks of corporate and confidential data.
- Active Dark Web Leak Monitoring System
The evaluation phase is one of analysis of an IT environment in order to determine in depth the strengths and opportunities for improvement. This phase, when well affirmed, demonstrates a certain maturity, because the organization obtains a formalized and external opinion to know its posture and can then improve it.
- ISO 27001 Audit
- Cybersecurity Audit
- Vulnerability Audit
- CGTI and NCA 315 audit (IT component)
- Audit process / procedures
- Website Audit
Penetration testing represents a further step in terms of maturity, since it represents an exhaustive preventive effort of the security of information assets. They are also often required in contexts of standardization and obtaining cyber insurance.
- External penetration testing
- Internal Penetration Testing
- Web Penetration Testing
- Application penetration tests
- Physical penetration tests
The prevention phase and the actions associated with it firmly affirm the maturity of an organization through awareness of risks and their management.
- Information Asset Inventory
- Cybersecurity risk analysis
- Automated vulnerability scanning
- Risk management strategy
The preparedness phase allows the organization to prepare for an incident that could affect its activities. While the plans created help theoretically prepare the organization, the simulations confirm their effectiveness and prepare the teams.
- Backup Management Directive
- Incident management plan
- IT Recovery Plan / Business Continuity Plan
- Investigation (prevention and investigation)
When an organization is confident in its maturity, it can consider having it recognized by opting for formal recognition associated with a recognized industry standard. Once obtained, it can demonstrate it to its customers, suppliers, investors and others.
- ISO27001
- SOC report
- PCI-DSS
- Cybersecure Canada
- And others
How is a cybersecurity maturity diagnosis carried out?
The maturity diagnostic is a summary assessment to determine where an organization is in its cybersecurity journey. It is a simplified tool for taking stock of what has been achieved, and what would be the next steps to grow your organization in terms of cybersecurity.
Our diagnosis takes place in 5 main steps.





The deliverable is a report that indicates the position of the company in the cybersecurity maturity scale with recommendations adapted to the observations made.
Why choose MS Solutions to carry out your cybersecurity diagnosis?
Our specialists have many years of experience and have many recognized and relevant CISA, CISSP, and ISO 27001 LI&LA certifications. In addition, our ISMS (information security management system) holds ISO 27001 certification. The qualification of our team members allows us to distinguish ourselves in the market.
Our engagement

Your projects are entrusted to cybersecurity professionals who proactively manage IT security for hundreds of Canadian companies.
Bernard Després
Safety and audit practice director
A company firmly established in Quebec

MS Solutions has a team of over 75 IT professionals. The company is experiencing sustained growth and is considered a leading player in the IT industry in Quebec. We are proud to have been in business for over 30 years!
Exceptional expertise in cybersecurity

Our penetration testing team will be able to advise you on the type of penetration testing or cybersecurity audits necessary for your business. Rest assured that our specialists will be able to offer you a service adapted to the specific needs of your organization.
In-depth expertise in penetration testing

Penetration testing projects are overseen by Bernard Després, partner and director of professional services, certified CISA (Certified Information Systems Auditor) and CISSP (Certified Information Systems Security Professional) with more than 20 years of experience in IT consulting.
News from the IT world
MDR: Your shield against cyberthreats
Faced with the explosion of cyber threats in Canada, should businesses be worried? In 2023, Canadian businesses suffered an average of 72 attacks per week, according to Statistics Canada. This…
Prevention rather than cure: Backup and recovery strategies for your business
Backing up corporate data is an essential practice for ensuring business continuity, protecting sensitive information and minimizing the risk of data loss. Over time, backup methods have undergone significant evolution,…
Demystifying ISO 27001: MS Solutions’ Journey to Success
ISO 27001 remains the international standard for information security management. Compliance with this standard can strengthen a company’s resilience and increase the confidence of its customers, suppliers and insurers. Through…
Microsoft Intune: secure, centralized device management
In a world of constant technological change, where working patterns are shifting towards hybrid configurations, including teleworking, and where equipment is evolving rapidly, thanks in particular to the “bring your…
Vigilance: are you getting the most out of the platform?
Considering that 82% of security breaches in an organization are the result of human error (Verizon, 2023), and that 1 in 5 email attacks is successful (Tessian, 2022), it’s safe…
5 steps to block spam on Outlook
Unwanted e-mails, also known as spam, can be a major nuisance in your inbox. On an organization-wide scale, they can not only reduce your productivity, but also have an impact…







