Support for compliance with Bill 25
Your compliance with Phase 1 and 2 of Bill 25, supported by our expertise

Ease of compliance
With our turnkey toolkit, you can easily comply with Bill 25 requirements.

Automation of your compliance
Thanks to the various document management tools in our toolbox, you will be able to automate the tasks related to your compliance.

Cybersecurity Expertise
Our hours of consultation with a cybersecurity specialist allow you to be advised to protect your precious data.
The turnkey toolbox integrated into Microsoft 365
Our turnkey toolkit integrated into Microsoft 365, developed in collaboration with the Delegatus collective of lawyers, provides you with all the tools you need to comply with Bill 25 Phase 1 and 2 compliance requirements.
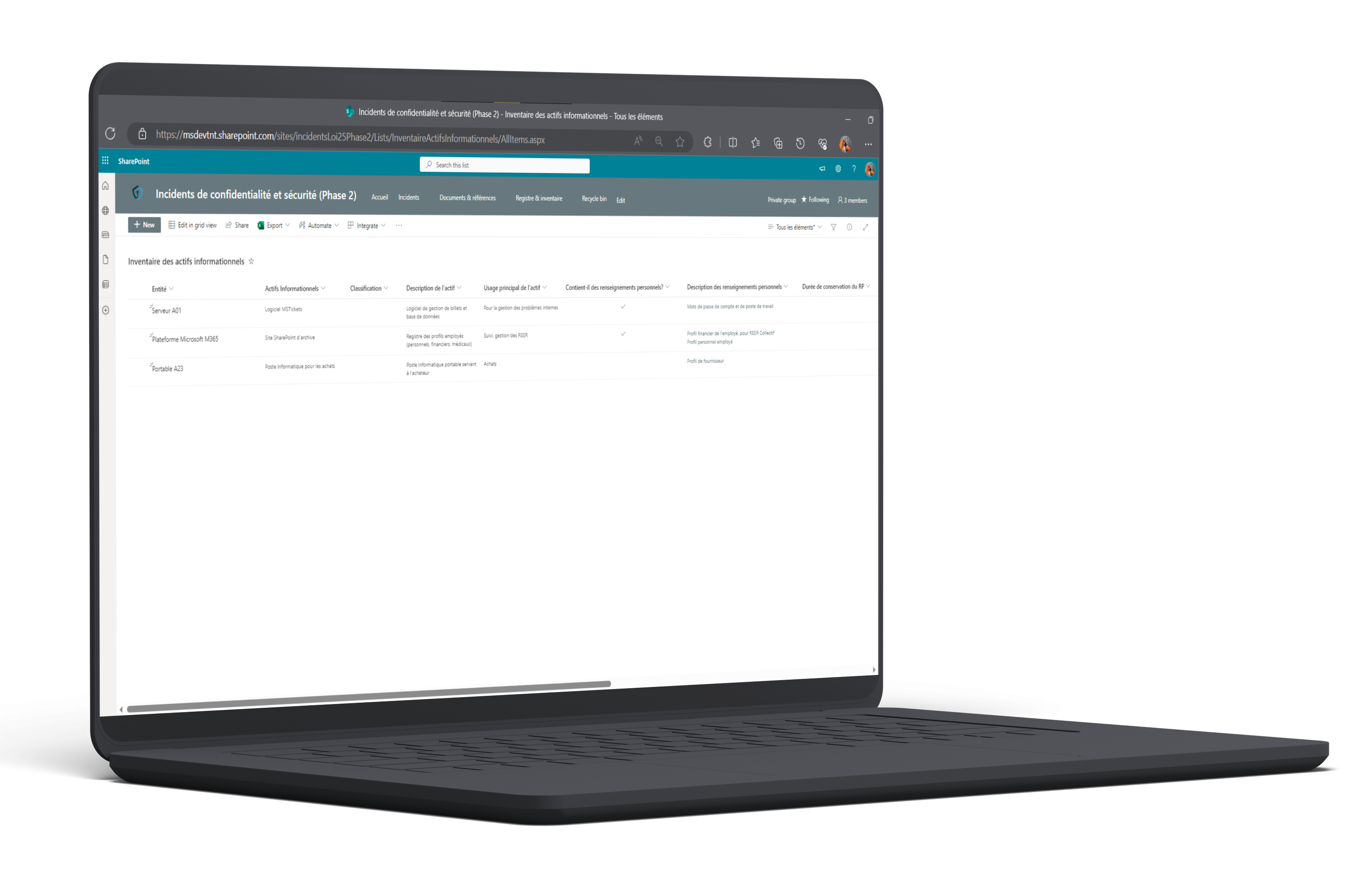
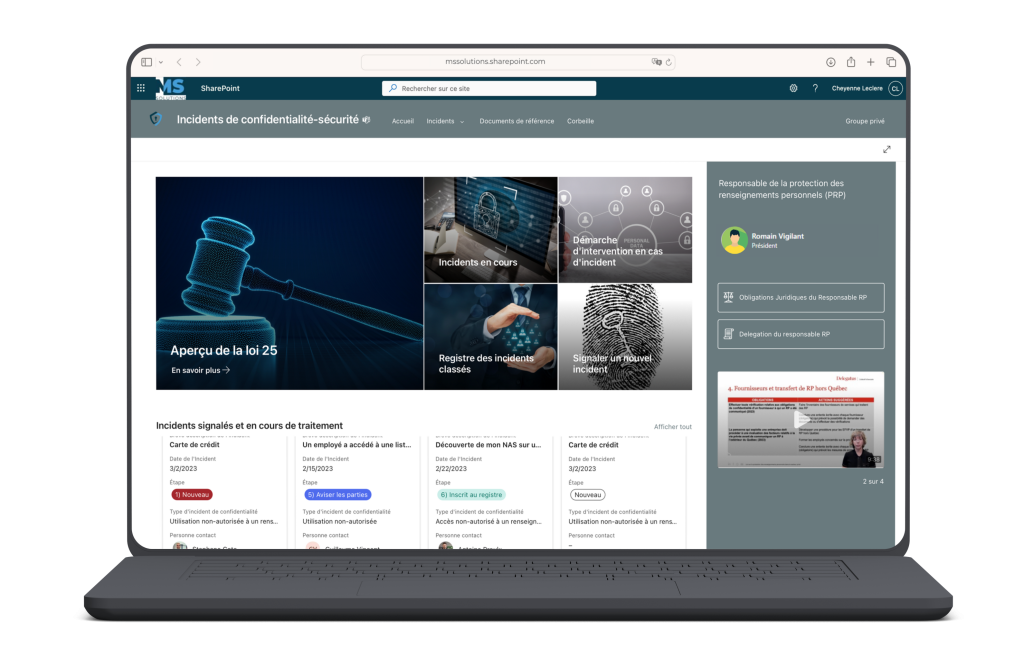
Our tunrkey toolkit includes a Privacy-Security Incident SharePoint Site.
It is possible to opt for this support in 2 separate stages (Phase 1 and/or Phase 2 of Bill 25)
Phase 1
Discover the inclusions of phase 1 below. Our support also includes an overview of the toolbox for the purpose of training the manager(s) and 5 hours of support with a cybersecurity specialist to ensure that your data is well protected.
Our turnkey toolkit integrated into Microsoft 365, developed in collaboration with the Delegatus collective of lawyers, provides you with all the tools necessary to meet the requirements of Bill 25.
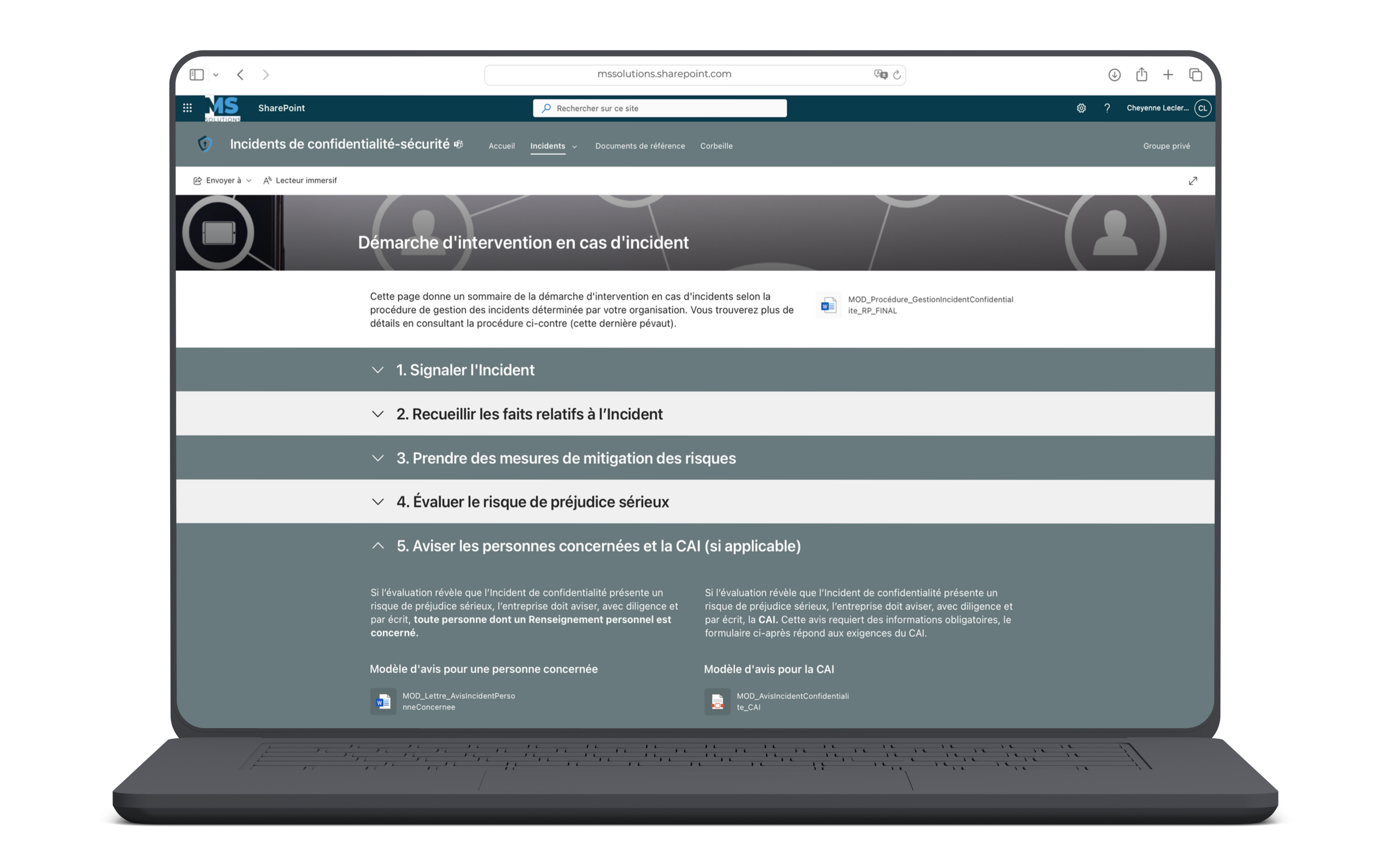
Privacy-Security Incidents SharePoint Site :
- Reference library with templates:
- Procedure for managing confidentiality incidents involving personal information
- Cybersecurity incident management procedure
- Model notice to notify in writing anyone affected by a privacy incident
- Model notice to the Commission d’accès à l’information (CAI)
- Analysis grid to determine if the incident presents a risk of serious harm
- Model of delegation of the manager and his legal obligations
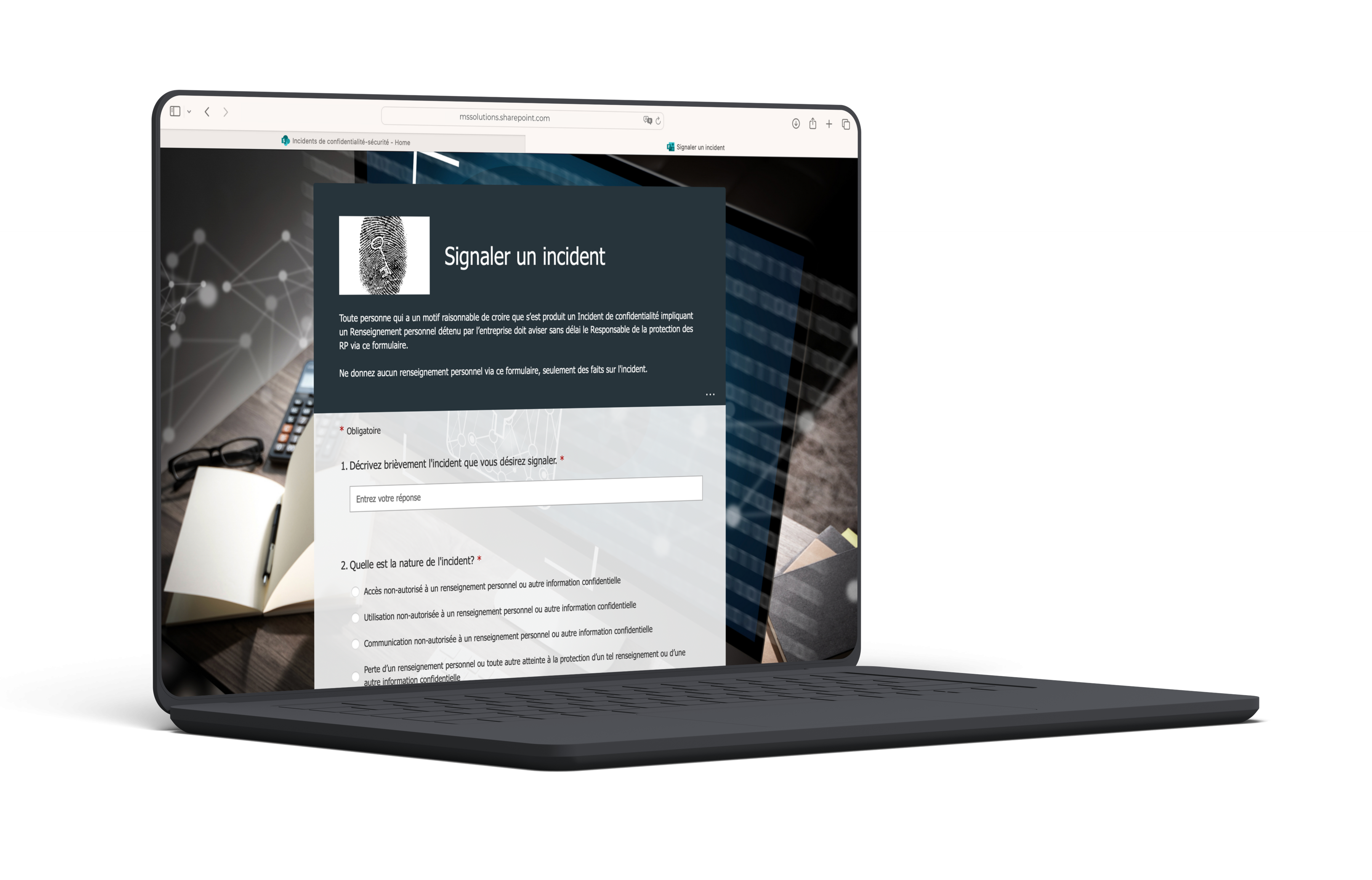
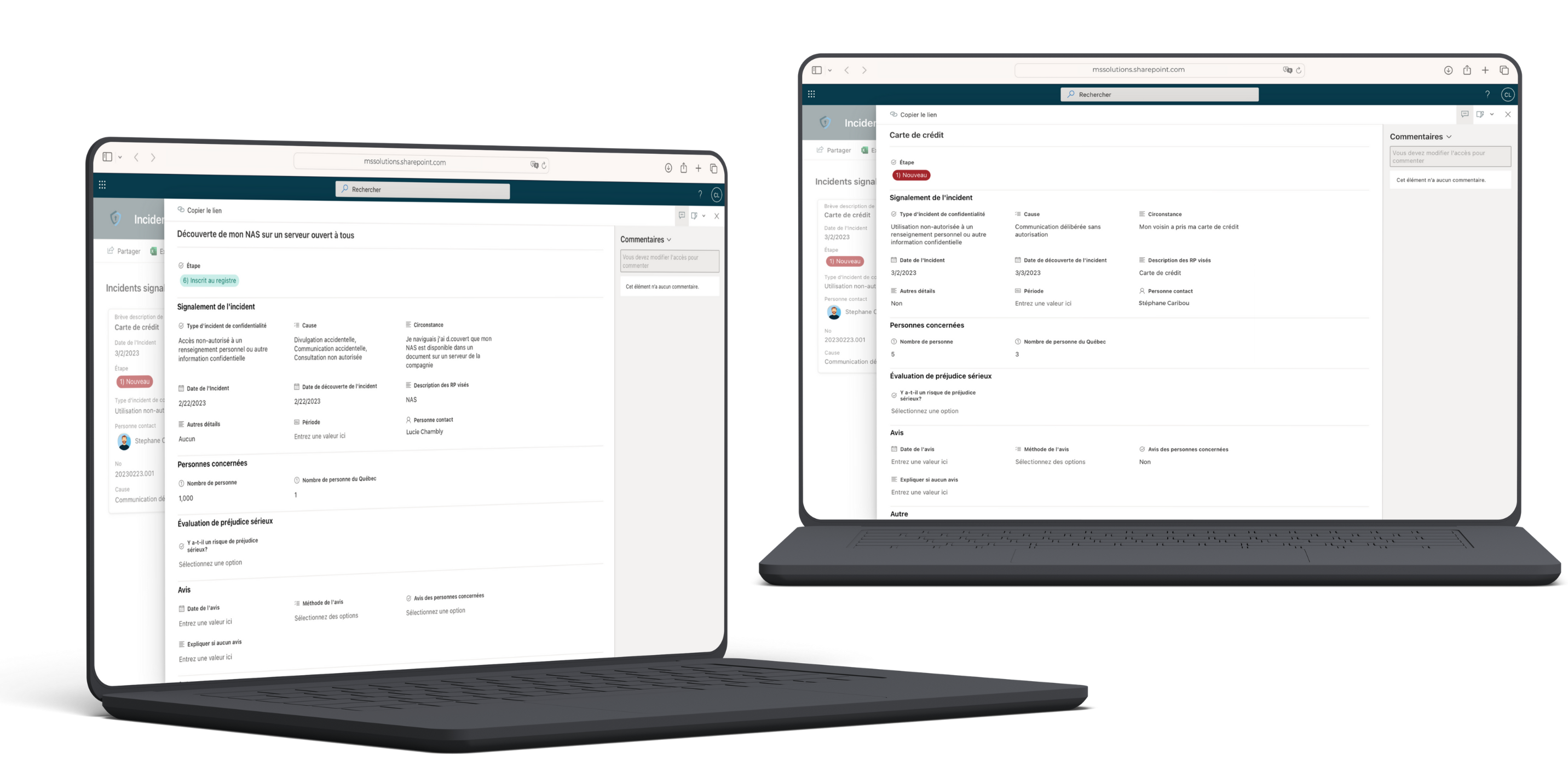
- Forms form for submitting privacy-security incidents
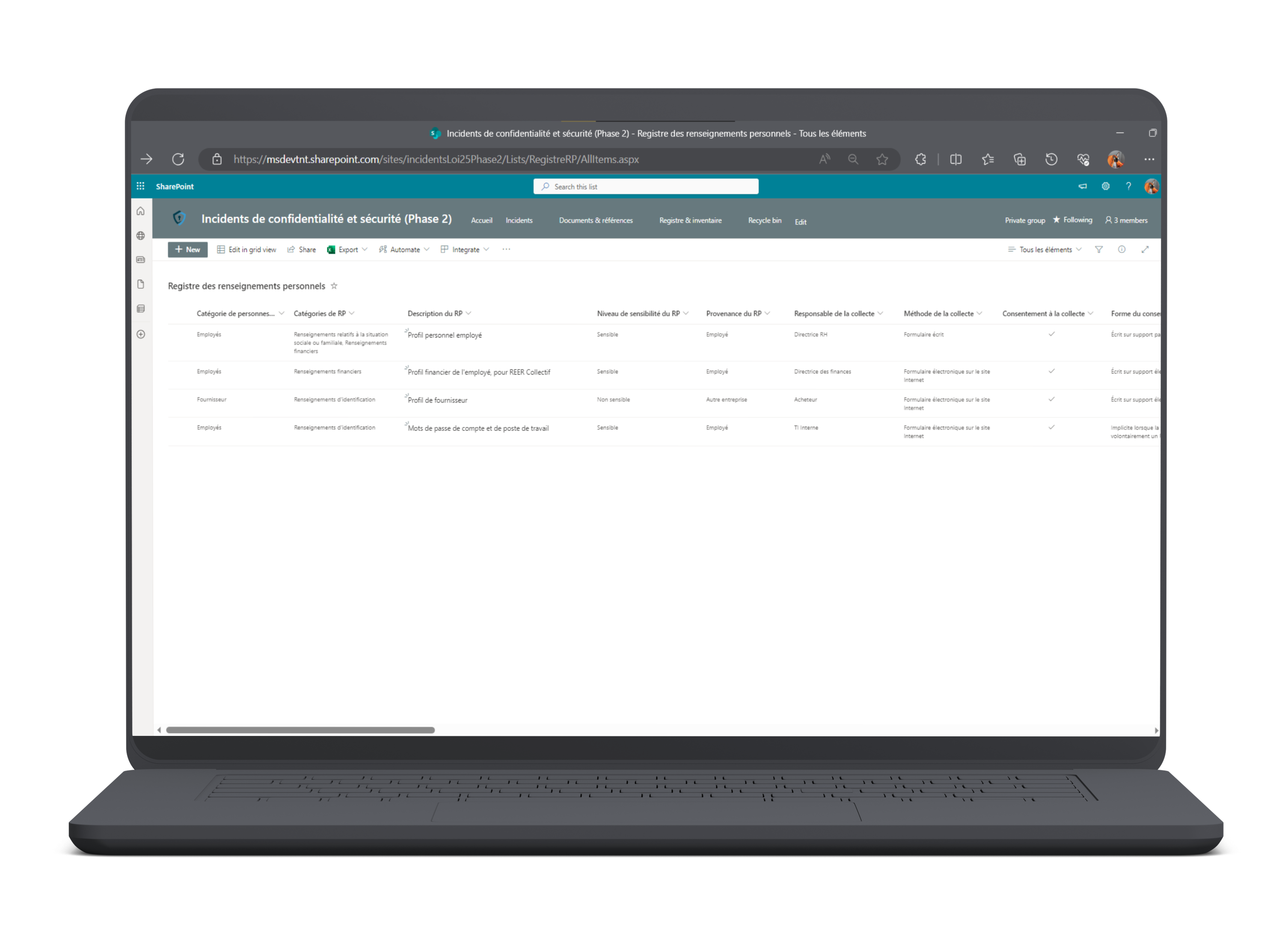
- Microsoft Lists Registry of Privacy-Security Incidents
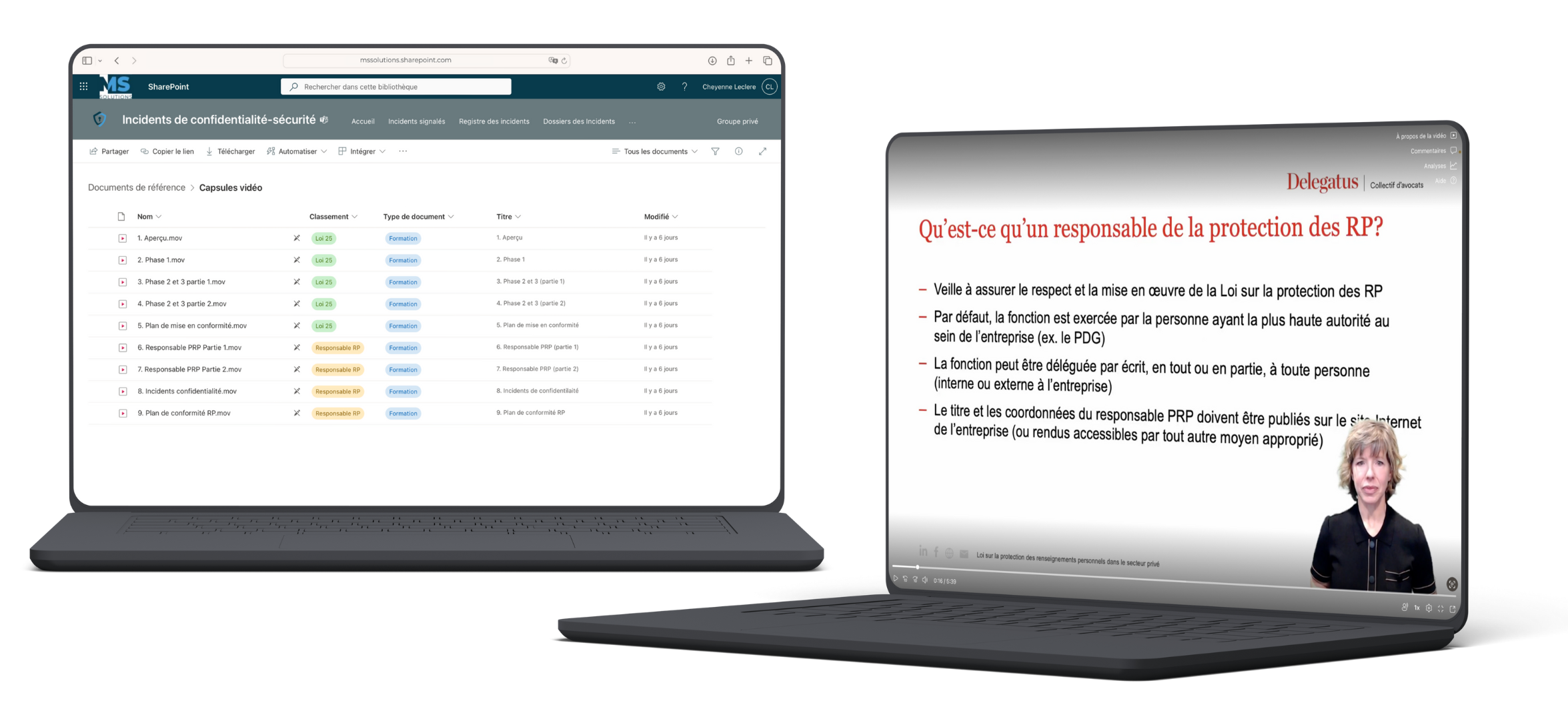
- Privacy Training Videos
- Overview of the toolbox for the purpose of training the manager(s)
Our turnkey toolbox includes 5 hours of consultation with our cybersecurity specialists to guide you in the protection of personal information.
Proper management of personal information requires optimal cybersecurity to ensure that no intruder can come and steal your precious data. Our team will be able to advise you on adopting a proactive attitude in the face of the inherent risks.
- Procedure for managing confidentiality incidents involving personal information
- Cybersecurity incident management procedure
- Notice template to notify in writing anyone affected by a privacy incident
- Model notice to the Commission d’accès à l’information (CAI)
- Analysis grid to determine if the incident presents a risk of serious harm
- Model of delegation of the manager and his legal obligations
Through this Forms form, anyone who has reasonable grounds to believe that a confidentiality incident has occurred involving personal information held by the organization can notify the Privacy Officer.
Our collaborators from the Delegatus law collective have created several video capsules to better understand what Bill 25 is about. We discuss the key terms (personal information, confidentiality-security incidents, person responsible for the protection of personal information, etc.) , but also the different phases of Bill 25.
To ensure that you have all the keys in hand to use your new tools, we do an overview of the toolbox with you for the purpose of training the manager(s).
Proper management of personal information requires optimal cybersecurity to ensure that no intruder can come and steal your precious data. Our team will be able to advise you to adopt a proactive attitude in the face of the inherent risks.
- Present and clarify incident management
- Respond to questions and queries related to incident management
- Specify the next steps for compliance with Bill 25 for your organization
* Up to 5 hours
Due to the legal implications linked to this compliance, our support includes a 45-minute consultation with a specialist lawyer.
Phase 2
Discover the inclusions of phase 2 below. Our à la carte support adapts to your needs in 3 formulas to choose from!
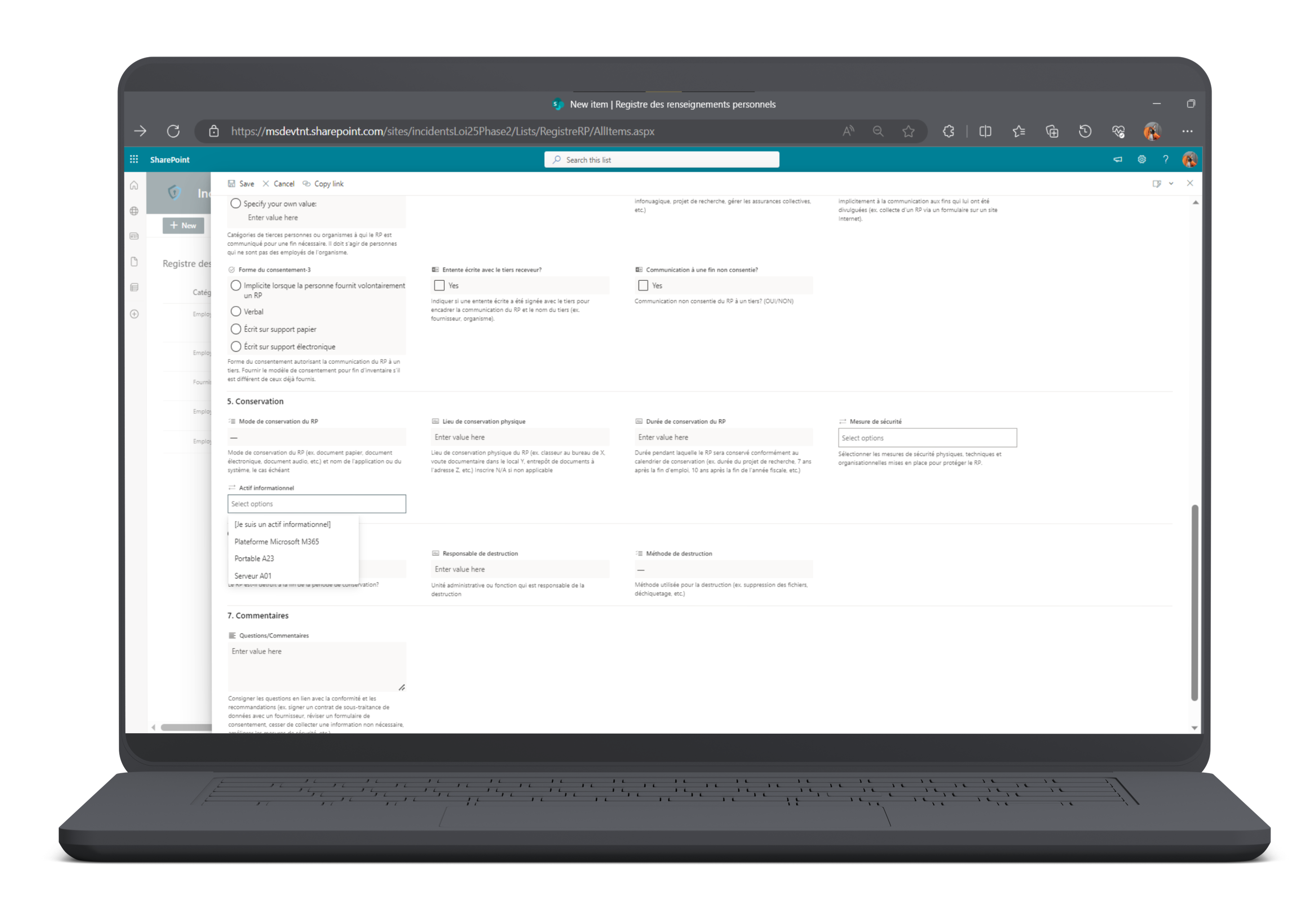
- Simple: Includes 5 hours of support to guide you in the method to adopt and the use of the Microsoft Lists registry to carry out your own inventory of your personal information
- Intermediate: Included 20 hours of support to carry out, with the necessary access, the inventory of your personal information and complete the register
- Complex: Assessment of specific support needs using a specialized technological tool for the inventory of personal information.
- Privacy Program
- Framework policy on the protection of personal information
- Directive on the Collection, Use and Disclosure of Personal Information
- Directive on the retention and destruction of personal information
- Procedure on the management of requests and complaints relating to personal information
- Directive on Physical, Technical and Organizational Security Measures for Personal Information
- Privacy policy for the website
- Contractual annex to be attached to a service contract to provide for the protection of personal information
- Data Processing Agreement as a Model Supplier Personal Information Processing Agreement
- Privacy Impact Assessment Guide
- Privacy Impact Assessment Report Template
For items that require legal support, we can put you in touch with a legal representative from the Delegatus lawyers’ collective.

Why be accompanied by cybersecurity professionals to comply with Bill 25?
Bill 25 modernizes the legislative provisions regarding the protection of personal information. Its purpose is to provide users with better control over their personal information.
To comply with the requirements of this law, organizations must implement several measures gradually.
3 phases are spread out in September 2022, September 2023 and September 2024.
- Getting support to ensure that you comply with all the prerequisites of Bill 25 makes it possible to not miss any of the crucial steps in data protection. We work closely with a legal team to ensure that our actions comply with the legal framework in force.
- Surrounding yourself with cybersecurity professionals to ensure the compliance of your data management is a good reflex. Indeed, our professionals are familiar with the topics of data governance and best practices to preserve the confidentiality of your data. In addition, good management of personal information requires optimal cybersecurity to ensure that no intruder can come and steal your precious data. Our team will be able to advise you on adopting a proactive attitude in the face of the inherent risks.

Our Commitment

Our team of certified cybersecurity professionals will work with you to implement and maintain the IT security solution that meets your needs.
Bernard Després
Security and Audit Practice Manager
Des nouvelles du monde des TI
The 10 most frequently asked questions about Bill 25
Bill 25, also known as “An Act to modernize legislative provisions relating to the protection of personal information”, came into force on September 22, 2022. This law aims to strengthen…
Bill 25 and SMEs, MS Solutions talks about it in Le journal de Québec
In a recent article on cybersecurity published in several major newspapers by Agence QMI (a Québec Media division), Simon Fontaine, Business IT Strategic Advisor at MS Solutions, addresses the obligations…
The main step of Bill 25 about the protection of personal information
Bill 25 modernizes Quebec’s privacy legislation. Its aim is to give users greater control over their personal information. To comply with the requirements of this law, organizations will have to…
Bill 25 and cybersecurity: are you ready?
If your organization stores sensitive personal data such as credit card numbers, social insurance numbers, or other confidential information about your customers or partners, you are covered by Bill 25. Indeed,…