Managed Cybersecurity Detection and Response Tool
Our solution provides continuous monitoring of your networks, endpoints and cloud environments, 24/7, to spot modern cyberattacks, respond quickly and facilitate recovery.
Our powerful tool minimizes and simplifies your involvement

For 30M
cyberattacks

Our tool filters 99%
alerts

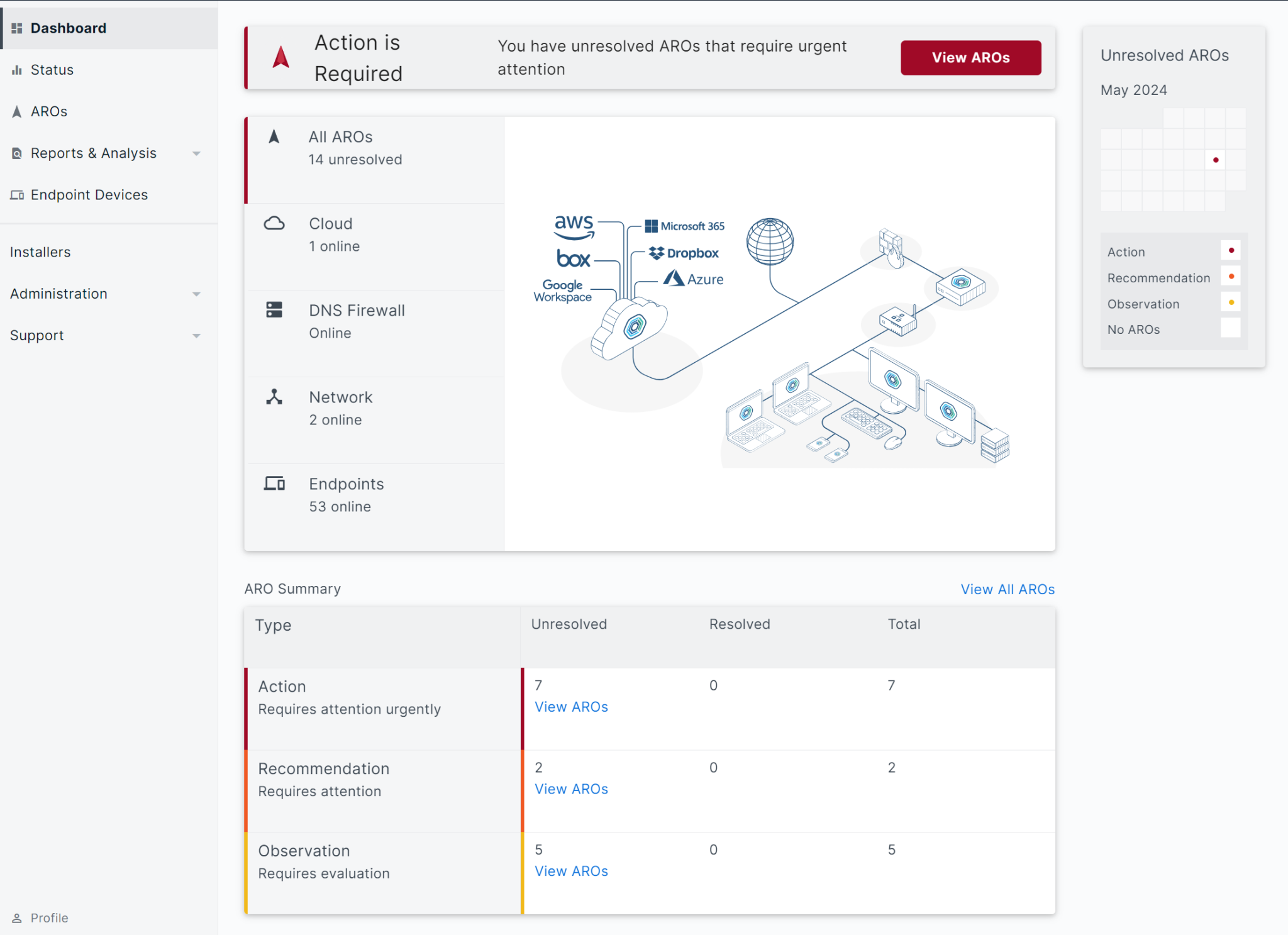
1 report “Actions, Recommendations and Observations”
We go beyond simple threat detection to spot, block and mitigate emerging risks while strengthening your security posture. Our managed cybersecurity detection and response service actively works to identify and understand the threats your environment is exposed to, helping to continually reduce the cyber risks you face.
- Comprehensive analysis of your environment to identify vulnerabilities putting your system and users at risk.
- 24/7 threat monitoring and detection to spot abnormal or suspicious behavior, early indicators of compromise or attack, with guidance on what action to take.
- Automatic neutralization of cyber threats and access to a proactive and flexible response plan to resolve threats faster.
Our managed cybersecurity detection and response solution is specifically designed to protect your entire attack surface against evolving threats. This approach eliminates security gaps between endpoints, networks and cloud services, ensuring reliable cybersecurity and peace of mind.
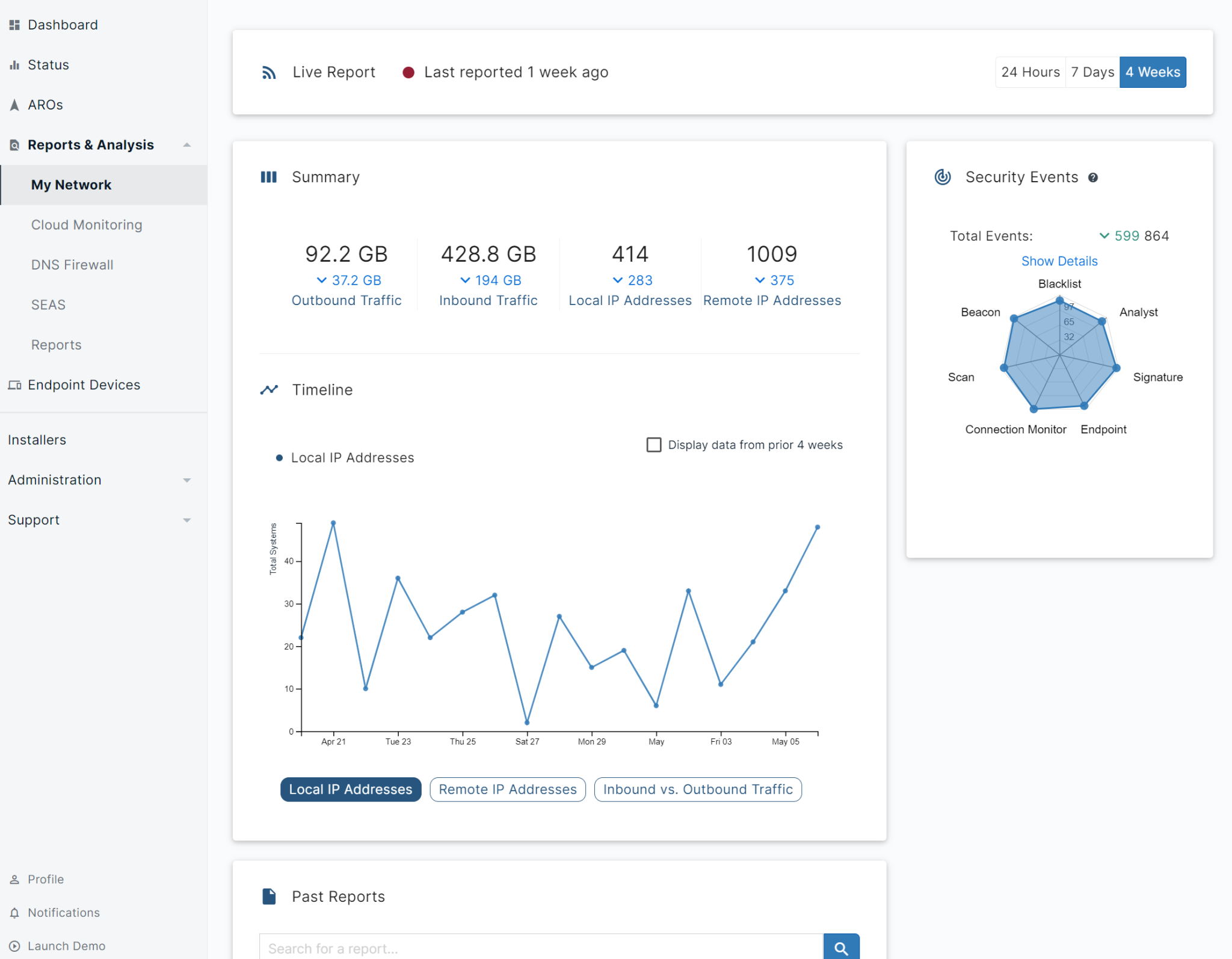
- Quickly identify threats and see a complete incident timeline with visibility into your endpoints, network and cloud services.
- Isolate and neutralize detected threats for 24/7 protection with our active response solution.
- Our experts provide proactive protection and monitoring to complement threat detection and identify vulnerabilities across your entire attack surface.
We filter out 99.9% of the noise generated by alerts to only present you with essential information. Powered by our proprietary scanning engine, our tool provides accurate, real-time threat detection.
- By aggregating analytics from endpoints, networks and cloud services, our tool provides a holistic, in-depth view of threats and their severity.
- Our tool automatically detects and addresses known threats, allowing our analysts to focus on investigating and stopping sophisticated threats, emerging risks and other anomalies early.
- Personalize our tool’s alerts for an even more precise match with your preferences and the normal functioning of your environment.
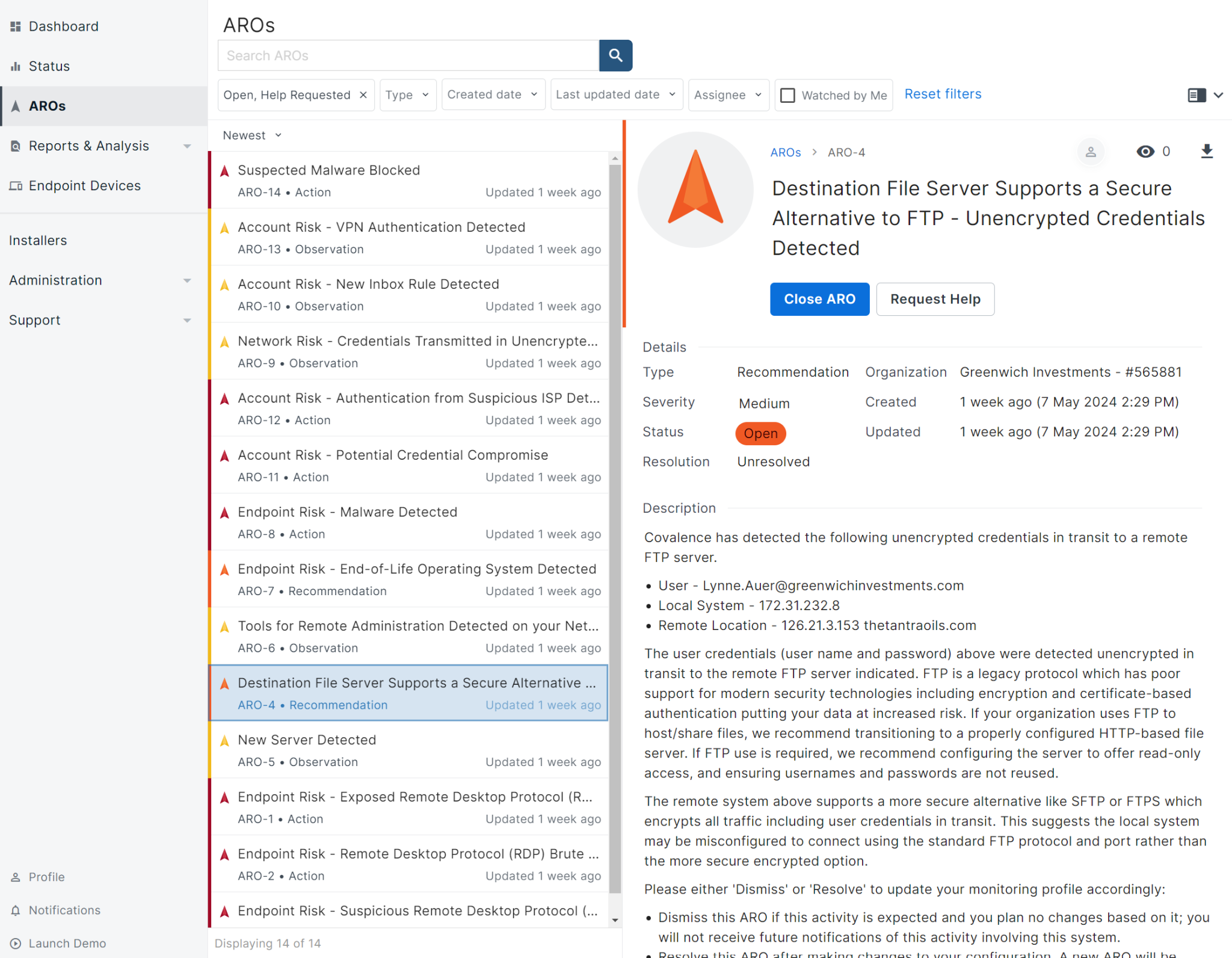
Our tool provides prioritized threat intelligence, accompanied by actionable actions through our proprietary ARO (Actions, Recommendations, Observations) system, providing comprehensive visualization and understanding of active threats and risks in one place.
- AROs go beyond simple alerts. They are fully prioritized and accompanied by clear recommendations for remediation, without technical jargon.
- Customize your thresholds to have our tool automatically apply fixes for certain ARO categories.
- With clear, easy-to-follow instructions, AROs strengthen IT teams’ ability to manage cybersecurity with confidence.
- See all relevant threat information at a glance, as well as all actions taken on your behalf.
Our managed cybersecurity detection and response tool in pictures
Discover the uncompromising simplicity of our user-friendly interface. Our tool provides an intuitive user experience, while offering a full range of features. Explore the ease of use of our solution for yourself and be amazed by its power.
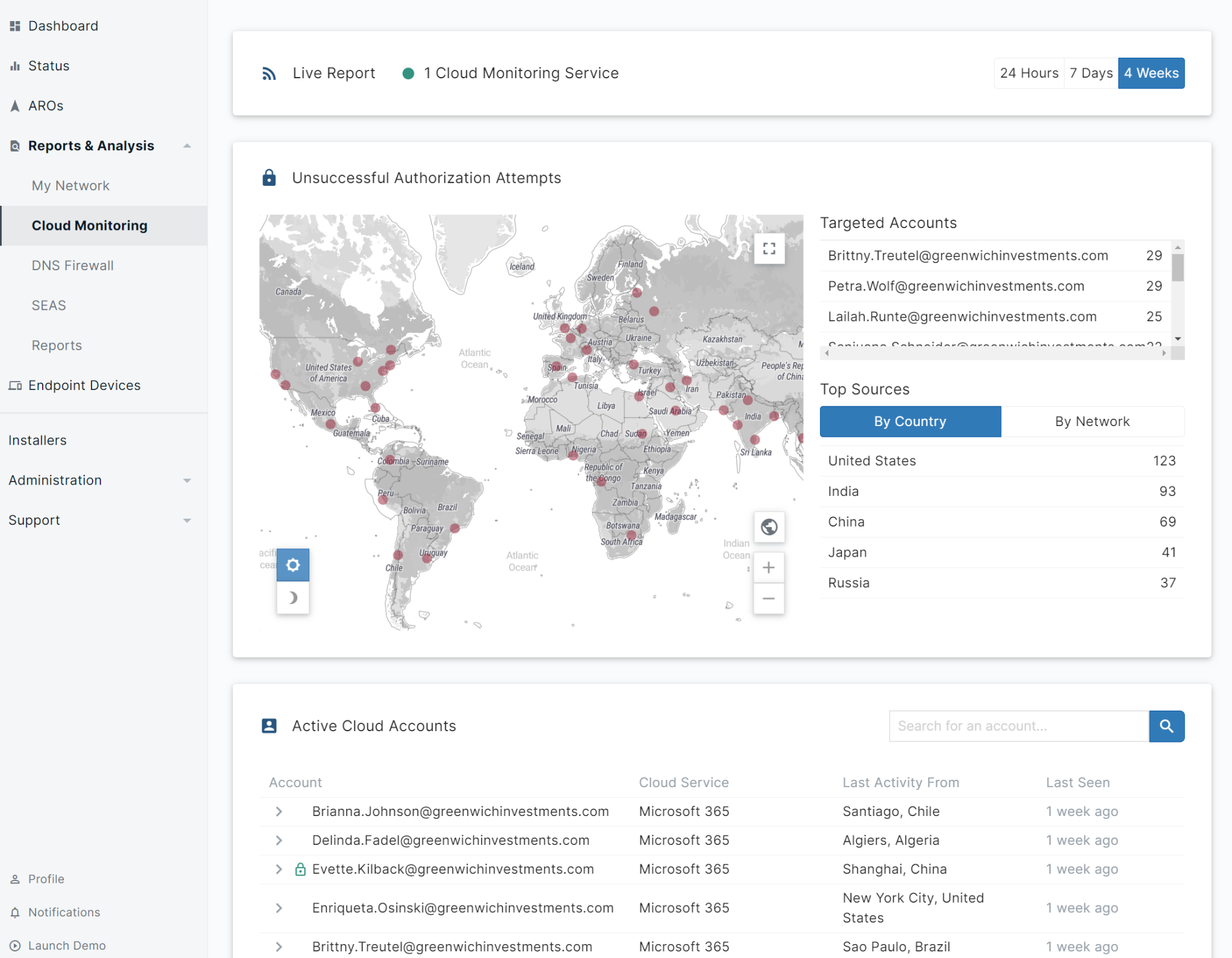
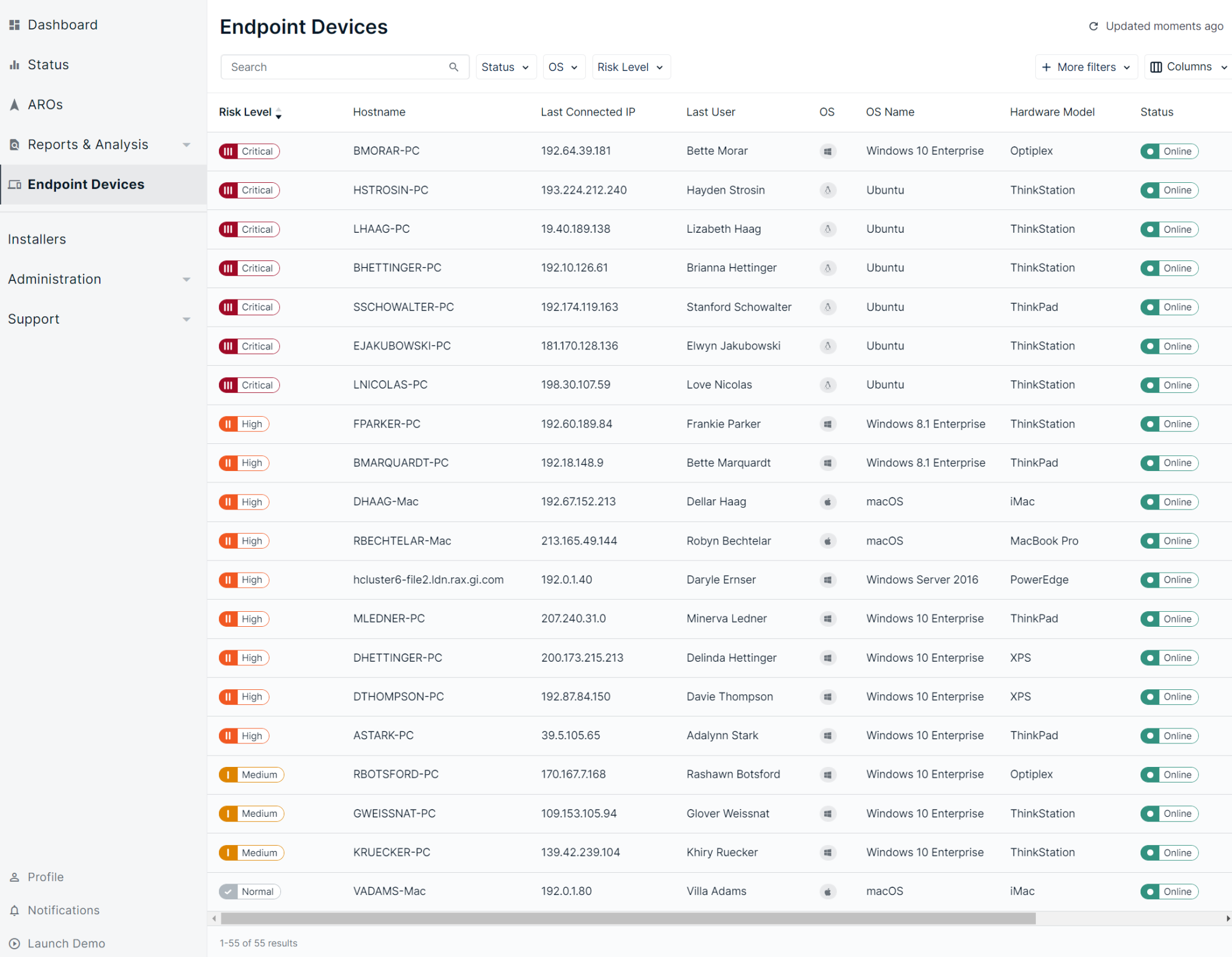
Did you know that…
Canadian businesses suffered an average of 72 cyberattacks per week in 2023.
Source: Canadian Cyber Security Center
F.A.Q
Find the questions most frequently asked by our visitors.
An MDR, or Managed Detection and Response, is a managed cybersecurity service that aims to detect, respond to and remediate threats proactively and continuously. Unlike a simple software solution or hardware device, an MDR combines advanced technological tools with human expertise to provide comprehensive protection against cyberattacks.
Here are the main aspects of an MDR service:
Continuous Monitoring: An MDR continuously monitors networks, systems, and endpoints to identify suspicious or malicious activity.
Advanced detection: Using technologies such as behavioral analytics, machine learning, and threat intelligence, an MDR is able to detect sophisticated and emerging threats that might evade traditional security systems.
Proactive Response: If a threat is detected, the MDR provider’s security teams respond quickly to contain and neutralize the threat, minimizing potential damage.
Remediation and Support: After addressing a threat, an MDR service helps remediate the damage caused and strengthen defenses to prevent future attacks.
Human Expertise: Unlike some automated solutions, MDR often involves human intervention, where trained security analysts review alerts and events to provide valuable insights and tailored responses to threats.
In summary, an MDR provides a proactive and comprehensive approach to information systems security by combining advanced technologies with expert human monitoring to detect, respond and remediate threats effectively and continuously.
Our MDR (Managed Detection and Response) service is aimed at a wide range of companies of all sizes and in all sectors of activity. Whether you are a small business, SME or large enterprise, our MDR can meet your IT security needs.
Companies that benefit the most from our MDR are often those facing a security skills shortage, looking to strengthen their security posture, or requiring proactive and ongoing monitoring of their IT environment. Our MDR service offers a comprehensive solution, combining advanced technology tools with human expertise to detect, respond and remediate threats effectively and continuously.
A SIEM, or Security Information and Event Management, is a software platform designed to collect, aggregate, standardize and analyze security data from various sources within a computer network. Its primary purpose is to provide complete visibility into security events and activities in an IT environment, enabling security teams to detect and respond to potential threats.
Here are some key features and functions of a SIEM:
Data Collection: A SIEM collects security data from various sources such as event logs, network feeds, authentication data, application logs, etc.
Aggregation and normalization: Collected data is aggregated and normalized to enable consistent analysis and correlation between events.
Event Analysis: A SIEM uses algorithms and predefined rules to analyze security events and detect suspicious behavior patterns or security incidents.
Event Correlation: It identifies relationships between different events to detect complex attacks that might go unnoticed if considered individually.
Alert generation: Based on the analyzes performed, a SIEM generates alerts to flag potentially malicious activities or abnormal security situations.
Secure Data Storage: It ensures secure, long-term storage of security data for regulatory compliance and post-incident analysis.
Reporting and Compliance: A SIEM provides reporting capabilities to help organizations meet compliance requirements and provide information on the status of network security.
In summary, a SIEM is a powerful solution used by organizations to monitor, detect, analyze and respond to IT security threats, providing extensive visibility into security activities and facilitating incident management.
It is a software solution installed on devices (endpoints) of a network, such as computers, servers, or mobile devices.
EDR monitors and records activity on these endpoints, detecting suspicious or malicious behavior.
However, EDR often requires human intervention for analysis and incident response.
The main difference between an MDR (Managed Detection and Response) and a SIEM (Security Information and Event Management) lies in their functionality and approach:
Functionality :
MDR (Managed Detection and Response): An MDR is a managed service that provides proactive and continuous monitoring of information systems. It combines advanced technological tools with human expertise to proactively and continuously detect, respond and remediate threats. MDR services often involve human intervention to analyze alerts, investigate incidents and provide an appropriate response.
SIEM (Security Information and Event Management): A SIEM is a software platform designed to collect, aggregate, standardize and analyze security data from various sources within an IT network. Its primary purpose is to provide complete visibility into security events and activities in an IT environment, enabling security teams to detect and respond to potential threats. A SIEM primarily focuses on collecting, analyzing, and correlating security data.
Approach :
MDR: The MDR takes a proactive and continuous approach to information systems security. It combines advanced technologies with expert human monitoring to detect, respond and remediate threats effectively and continuously.
SIEM: SIEM provides visibility into security events and activities in an IT environment, but it is often used reactively to analyze security data and detect threats. Security teams typically use a SIEM to monitor, detect, and respond to security incidents.
In summary, while MDR provides proactive, continuous monitoring with human intervention to detect, respond, and remediate threats, SIEM focuses on collecting, analyzing, and correlating security data to provide visibility into security data. security events and activities in an IT environment.
The main difference between an MDR (Managed Detection and Response) and an EDR (Endpoint Detection and Response) lies in their functionality and approach:
Functionality :
MDR (Managed Detection and Response): An MDR is a managed service that provides proactive and continuous monitoring of information systems. It combines advanced technological tools with human expertise to proactively and continuously detect, respond and remediate threats. MDR services often involve human intervention to analyze alerts, investigate incidents and provide an appropriate response.
EDR (Endpoint Detection and Response): EDR is a technology focused on detection and response at endpoints, such as computers and servers. It monitors and records activities on these devices to detect suspicious or malicious behavior.
Approach :
MDR: The MDR takes a proactive and continuous approach to information systems security. It combines advanced technologies with expert human monitoring to detect, respond and remediate threats effectively and continuously.
EDR : EDR primarily focuses on detection and response at endpoints. It may require human intervention for alert analysis and incident response.
In summary, MDR addresses the skills shortage faced by many organizations, providing a comprehensive solution, while EDR provides crucial visibility and management of workplace security. Businesses are encouraged to adopt the most suitable solutions to address all their security challenges, which often involves using EDR and MDR together.
Our MDR solution is a central element in complying with cyber insurance requirements, although it is not the only factor to consider.
To learn more about cyber insurance, do not hesitate to consult our dedicated blog article on the subject: Cybersecurity Insurance : An essential investment for the digital age
No, our MDR solution is not just for Microsoft 365 environments.
Yes, our MDR solution is also accessible via a mobile interface, allowing you to monitor your environment at any time. Additionally, you can configure your notifications to receive SMS alerts and mobile notifications.
If you have a IT managed services plan with MS Solutions, we can take care of the management of alerts sent by the MDR (additional charges may apply).
If your company prefers to internalize alert management via its IT team, this is entirely possible thanks to the simplicity of our interface. A one-off consultation by our professionals is also available.
Notre engagement

Vos projets sont confiés à des professionnels en cybersécurité qui gèrent de façon proactive la sécurité informatique pour des centaines d’entreprises canadiennes.
Bernard Després
Directeur pratique sécurité et audits
Des nouvelles du monde des TI
Vigilance: are you getting the most out of the platform?
Considering that 82% of security breaches in an organization are the result of human error (Verizon, 2023), and that 1 in 5 email attacks is successful (Tessian, 2022), it’s safe…
Avoid the risks of phishing
Phishing is a technique used by hackers to try to trick users into clicking on dangerous links or asking them to share sensitive information. Phishing attacks can take many forms,…
Vigilance, Our Ongoing Phishing Awareness Platform
In a recent webinar, we discussed the importance of continuous phishing awareness. Thus, we took the opportunity to present our platform: Vigilance + – whose goal is to keep employees…
Cybersecurity: Think About The Safety Of Your Employees
It is important to recognize the threats that your IT environment may face, in order to anticipate them and act proactively. It is therefore essential for everyone, from business owners…
Change your passwords!
Do you tend to use the same passwords all the time? A few weeks ago, we alerted you to a security breach at LinkedIn and briefly informed you about the…
Cybersecurity for small and medium-sized businesses in 5 questions
The number of computer attacks is constantly evolving: data theft, ransom demands, image damage… This often has serious or even irreversible consequences. Small and medium-sized companies are the most affected…







