More than six out of ten SMEs in Quebec (63%) have suffered a cyberattack in the last year (Source: KPMG Survey). In addition to being costly, cyberattacks can damage your company’s reputation. Fortunately, there are simple and effective strategies to strengthen your cybersecurity, accessible no matter the size of your organization.
In this article, we will reveal three strategies that will help you protect your organization against online threats. Whether you’re a CEO, IT manager, or just a security-conscious employee in your business, these strategies are for you.
1. Geofencing
What is Geofencing
Geofencing consists of virtually delimiting a geographical area to limit access to sensitive information. Geofencing allows you to define policies and controls based on the origin of an action or connection. (The origin GPS, RFID, IP address or others…)
By using this technique, any organization can thus restrict access to its data only to people who are in a specific and authorized place.
Why you should use this strategy
Geofencing aims to better control the origin of connections to sensitive data in order to enhance security and protection against malicious attacks. Thus, organizations can reduce the risk of data leaks, hacks and privacy breaches.
This strategy is generally easy to set up and manage, which makes it accessible even for organizations that do not have a large budget to allocate to cybersecurity!
Here are the main lines for programming these conditional accesses:
- Define the list of legitimate countries to establish connections to Microsoft 365
- Configure named locations to declare legitimate countries
- Create policies that block access to Microsoft 365 for everyone by default
- Adjust policy to exclude certain named locations
- Define the scope of the policy to users or groups of users
- Operationalize adjustments to the strategy to meet specific needs
Advice from MS Solutions: Any organization that has opted for Microsoft and has a Business Premium license can benefit from geofencing.
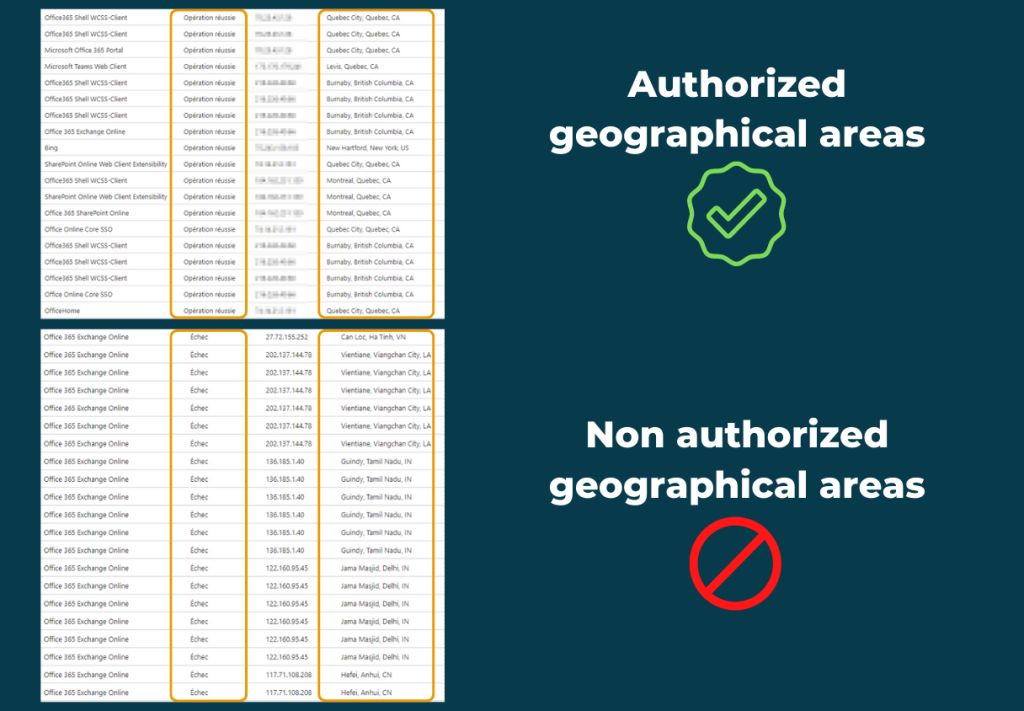
Here is a real-life example of all failed login attempts thanks to geofencing
2. Dark Web Monitoring
The Dark Web is a hidden collection of Internet sites that can only be accessed by a specially designed browser. It is used to preserve the anonymity and confidentiality of activities on the Internet. For this reason, the Dark Web is the perfect place for computer criminals to be able to exchange information in a perfectly… illegal way!
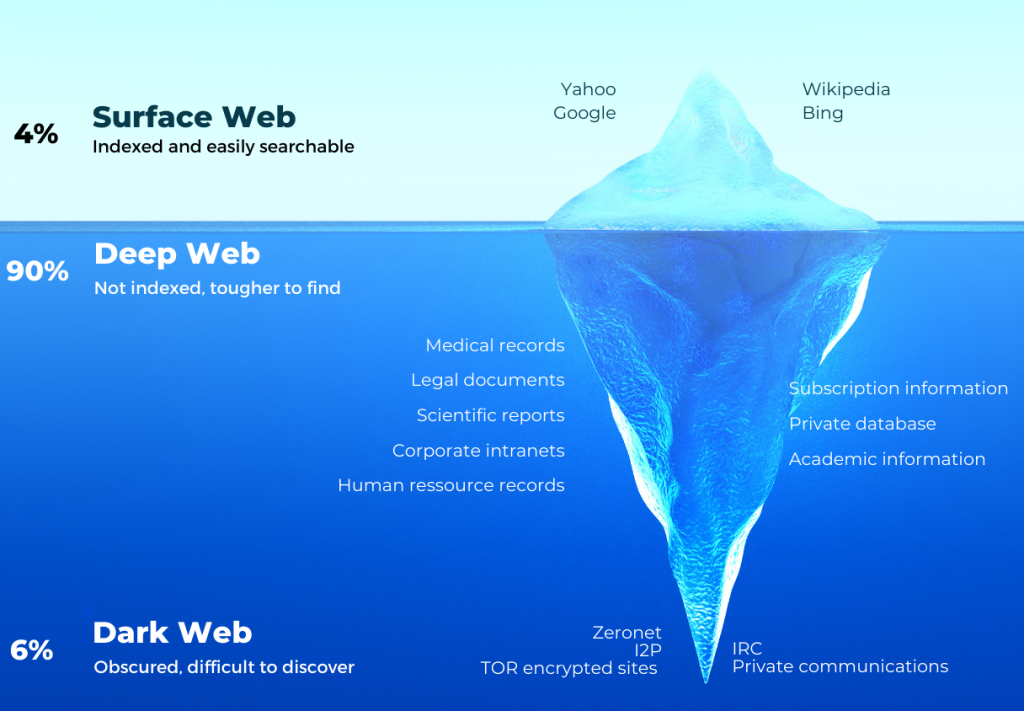
Dark Web monitoring is the process of tracking and tracking information about your organization that is leaked on the Dark Web without your knowledge. When your information is leaked on the Dark Web, it is important to promptly take corrective measures so that it cannot be used by multiple malicious actors.
At MS Solutions, our proactive Dark Web data monitoring service allows our customers to be alerted when employee emails and passwords are found for sale to the highest bidders on the Dark Web.
Nearly 2/3 companies worldwide, and 63% in Canada have seen an increase in targeted cyberattacks since they turned to teleworking. (Source: Radio-Canada) These figures are alarming, which is why it is important to opt for a surveillance strategy as soon as possible.
To learn more, here is an article that might interest you: Make Dark Web Monitoring a Priority
3. Continuous cybersecurity awareness and phishing simulation
When you know that human error is the cause of 95% of cybersecurity breaches (Source: IBM), it goes without saying that it is essential to educate your team about cybersecurity to minimize the risk. By regularly training employees on cybersecurity best practices and showing them how to deal with phishing situations, organizations can strengthen the protection of their network.
Just as cyberattack techniques are evolving, so are awareness methods. A few years ago, organizations were content to train employees, and to do, at best, a simulation of a phishing attempt on an ad hoc basis.
Nowadays, the means made available have evolved, because we have understood that raising awareness once a year was not enough to respond to an omnipresent risk. For this reason, there are now continuous phishing simulation platforms that keep your employees alert at all times.

Additionally, by conducting regular phishing simulations, organizations can test and improve their defense against cyber threats by keeping users on top of their game.
In short
No matter the size of your organization, cybersecurity is a crucial issue to guarantee its survival. It is therefore important to take concrete measures to protect your company and your sensitive data. The three strategies we discussed – geofencing, dark web monitoring, and cybersecurity awareness – are simple to implement and effective.
Keep in mind that in terms of cybersecurity it is much less costly to act in prevention than in remediation. We advise you to integrate them into your cybersecurity strategy today to strengthen the protection of your organization. Remember that cybersecurity is an ever-evolving process, so it’s important to stay informed and continue to take steps to protect yourself.
If you would like to learn more about our cybersecurity solutions, conctact our experts to discuss your needs and concerns.