An IT assessment allows you to obtain a factual report on the state of your IT infrastructure, both in terms of security and performance. Thanks to an in-depth analysis of your IT equipment and its functioning, you will obtain a complete vision of the state of your IT services. Carried out by a third-party company specializing in the field, any problems or flaws in your IT infrastructure will be detected upstream.
When to request an IT assessment?
We recommend that you carry out an IT Assessment once a year to prevent possible system problems before they become too serious and to carry out a complete security check. If you postpone the audit over time, the intervention costs once the system is down or during a cyber attack will be much more costly for your company. In addition, as technologies are constantly evolving, a regular IT assessment will ensure that your system is up to date and protected from possible computer attacks.
The IT assessment to ensure the performance and security of your business:
A complete audit includes a performance-based component, which will review your facilities and the daily uses of your employees with the tools and software put in place. By analyzing the current situation of your IT services, the company carrying out the audit will be able to identify the strengths and vulnerabilities of your IT equipment. At the same time, an analysis of the state of IT security will be carried out as well as an analysis of all your IT equipment: networking, servers, storage, etc.
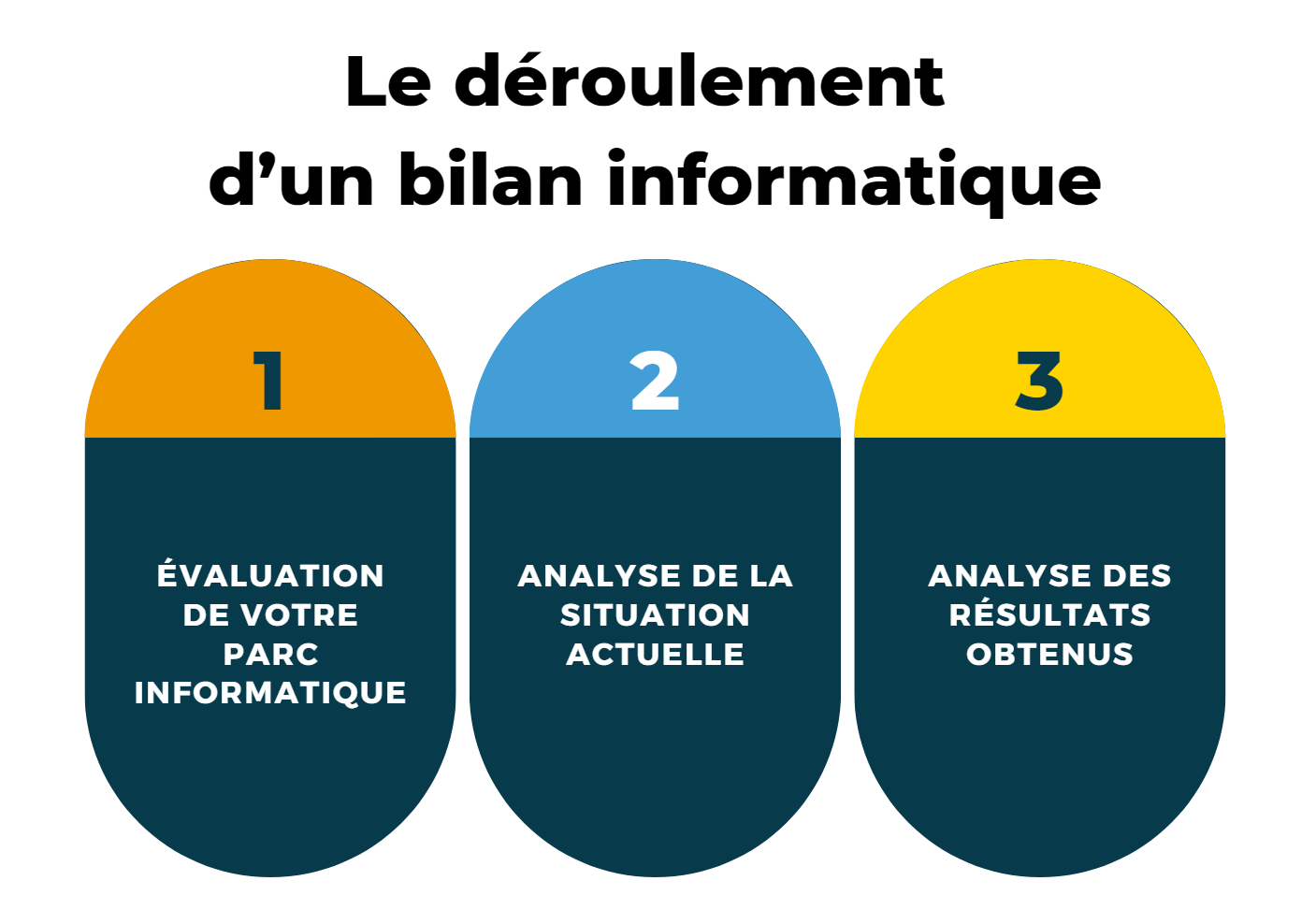
At MS Solutions, your IT assessment takes place in 3 main stages:
- Evaluation of your IT equipment
Our experts will search for basic information in order to have on hand all the elements necessary for the IT assessment. We will begin the IT assessment with an inventory of the critical equipment in your IT fleet.
2. Analysis of the current situation
This analysis will include a summary analysis of the situation, the strengths and vulnerabilities associated with the current situation as well as an analysis of your perimeter security.
3. Analysis of the results obtained and writing of the report
We will provide you with a report which will include a summary assessment of vulnerabilities, a status report, a situation report and the state of your perimeter security.
What actions should you take once the audit has been completed?
Once the audit is complete, you will receive a report with recommendations. You can then decide to resolve the flaws and problems internally or to entrust them to the company that carried out the audit. Therefore, you will need to ask yourself the right questions: Do you have the resources internally? Which solution will be the quickest and most effective? Which will be the least expensive? By answering these questions, you will be able to make an informed choice. MS Solutions offers different services with experts specialized in each of them: Cybersecurity, Managed IT Services, Cloud Services, etc.
Ready for your annual IT audit?
MS Solutions has several years of experience in IT audits. Do not hesitate to contact us to discuss your company and your needs, our experts will be there to listen to you. Contact us or request a quote by clicking here.